Using Temporary Access Pass in Azure AD for account access recovery
Microsoft has defined a four-step approach to end the era of passwords:
Source: Microsoft
As part of the passwordless deployment solution, Temporary Access Pass simplifies and secures the account onboarding experience for the end user. It also makes account access recovery easier by using time limited passcodes to sign in and then allowing the end user to re-register for a new strong authentication methods in situations where the user has lost or forgotten their authentication factors like a FIDO2 security key or Microsoft Authenticator app. In this blog I am going to cover the steps of enabling TAP and what the end user experience looks like when trying to recover an account.
In order to sign in with a Temporary Access Pass, TAP needs to be enabled in the authentication method policy. Although one can create a Temporary Access Pass for any user, only those included in the policy can sign-in with it.
Note: Only Global administrator and Authentication Method Policy administrator role holders can update the Temporary Access Pass authentication method policy.
Enable TAP in Azure AD
1. Navigate to Azure Active Directory > Security > Authentication methods > Temporary Access Pass.
2. Click Yes to enable the policy, select which users have the policy applied.
Default TAP settings can be changed if needed.
Note: If the intended user is not targeted, then on trying to create a TAP for the user, you will see the following error.
Therefore, please make sure to enable the users for the TAP policy under authentication methods.
Create TAP for users
1. Navigate to Azure Active Directory > Users > Select the user > Authentication methods
2. Select the option to Add authentication methods > Temporary Access Pass
3. If needed, define a custom activation time or duration and click Add.
4. Once added, the details of the Temporary Access Pass are visible which needs to be provided to the intended user.
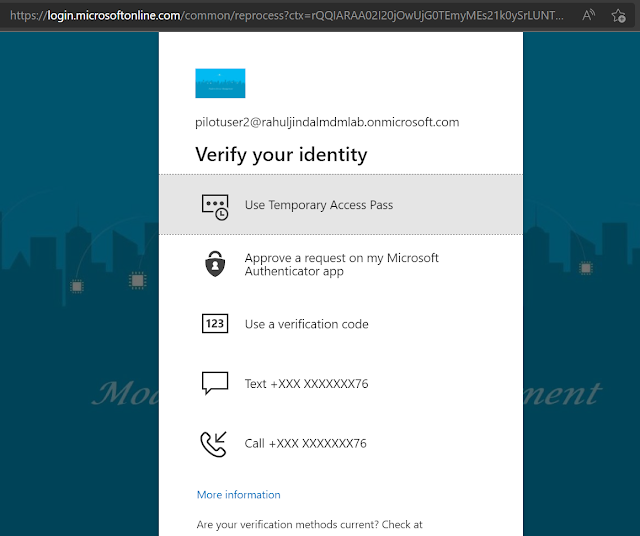
Admin should ask the users to authenticate to aka.ms/mysecurityinfo to authenticate using TAP and re-register their authentication methods like Authenticator app. After providing the user name, the user will immediately be presented with the option to provide TAP. At this stage, if the user does not know or has forgotten their password, then they should use TAP to login.
User will not be asked to MFA, but TAP will be available as an additional authentication option for the user until the TAP policy expires.
Once in, the user can then re-register for a strong authentication method.
Admins can refer to sign-in logs in Azure to verify for TAP as an authentication method as well.
Conclusion
It is worth noting that TAP doesn't replace a user's password and that a user can only have one Temporary Access Pass. If the user requires a new Temporary Access Pass, then the admin will need to delete the existing TAP and create a new one. This is also true for TAP that have expired. Users who update their authentication methods due to losing their credentials or device should make sure to remove the old authentication methods.












Comments
Post a Comment