Passwordless phone sign-in with the Microsoft Authenticator app
As part of my blogging series for implementing Azure AD authentication methods, I wanted to now cover passwordless authentication. Many organizations don't enable passwordless authentication because they think pins are less secure, but a username and password remains a primary attack vector and weak form of authentication that can be abused by bad actors through the means of social engineering, phishing, and spray attacks to compromise passwords.
A passwordless authentication strategy mitigates the risk of these attacks as the authentication methods are more convenient because the password is removed and replaced with something you have, plus something you are or something you know.
Microsoft global Azure and Azure Government offer the following three passwordless authentication options that integrate with Azure Active Directory (Azure AD):
Source: Microsoft
The Microsoft Authenticator app can be used to sign in to any Azure AD account without using a password. Microsoft Authenticator uses key-based authentication to enable a user credential that is tied to a device, where the device uses a PIN or biometric. This authentication technology can be used on any device platform, including mobile. This technology can also be used with any app or website that integrates with Microsoft Authentication Libraries.
Note: To get the full functionality of passwordless authentication, it is recommended that registration for Azure AD Multi-Factor Authentication and self-service password reset (SSPR) is enabled. You can quickly register for both at the same time by using combined registration. I published a blog on this very feature not so while ago which you can access over here.
There are of course some pre-requisites for using passwordless sign-in with Microsoft Authenticator App:
- Azure AD Multi-Factor Authentication is recommended with push notifications allowed as a verification method.
- Latest version of Microsoft Authenticator installed on devices running iOS 8.0 or greater, or Android 6.0 or greater.
- The device on which the Microsoft Authenticator app is installed must be registered within the Azure AD tenant to an individual user.
Enable Passwordless sign-in using Microsoft Authenticator app
1. Sign in to the Azure portal with a minimum permission of authentication policy administrator account.
2. Search for and select Azure Active Directory, then browse to Security > Authentication methods > Policies.
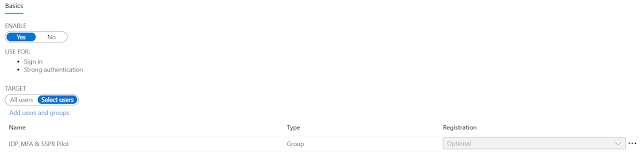
3. Under Microsoft Authenticator, choose the following options:
Enable - Yes
Target - All users or Select users group
Note: If you select individual users, then you will not be able to configure Require number matching & Show Additional context notifications as Enabled. You will have to let Microsoft manage it which in my opinion is not that consistent.
4. For the selected group, browse to ... > Configure.
5. Then for Authentication mode select Passwordless.
Note: Choosing Push prevents the use of the passwordless phone sign-in credential.
6. Then select Require number matching as Enabled.
7. After this select Show Additional context notifications as Enabled.
5. To apply the new policy, click Save.
End user experience
The first time a user starts the phone sign-in process, the user performs the following steps:
1. The user enters their name at the sign-in page.
2. If necessary, selects Other ways to sign in.
3. Selects Approve a request on my Microsoft Authenticator app.
4. The user is then presented with a number. The app prompts the user to authenticate by typing the appropriate number, instead of by entering a password.
After the user has utilized passwordless phone sign-in, the app continues to guide the user through this method. However, the user will see the option to choose another method.
Conclusion
Microsoft's passwordless authentication methods supports many scenarios. Each scenario comes with its own set of prerequisites, and capabilities. Organizations need to evaluate each authentication method and select the ones that suits their security needs. Once done, then organizations can plan the roll out and this particularly important. If not done correctly, the end result can be very disruptive and leave the end users very annoyed. Organization should first test the authentication methods against a pilot group and then slowly roll them out in production. To help organizations determine the appropriate authentication methods, Microsoft have provided a wizard as a good starting point. It can be accessed using https://aka.ms/passwordlesswizard.
Until next time..









Comments
Post a Comment