Intune: Windows Hello for Business
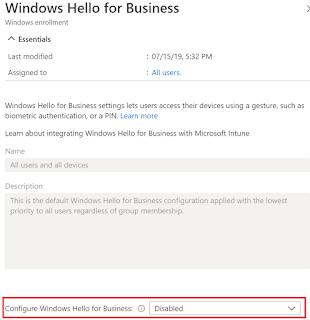
Windows Hello for Business has been aroun d for some time as an alternative sign-in method and it allows a user gesture to sign-in instead of just using a password. There are many sign-in gestures available and depending on what is supported based on the hardware, one can configure a PIN, biometric or a fingerprint. For corporate devices, PIN is the most suited method and it is easily configurable on Intune managed devices. However, I will cover other settings in this blog as well. Now Windows Hello for Business is Not Configured by default. So, in case you do not want to enable it for all your users (Remember this setting is a tenant wide setting) then you will need to atleast configure it to Disable for Intune to be able to manage the feature. Once in place, one can then deploy a Windows Identity protection profile policy to devices of your choice to enable the feature along with the desired configuration. Let’s begin Browse to Devices – Windows – Configuration profile.

