Enabling Windows 11 22H2 Core Isolation Memory Integrity feature using Intune

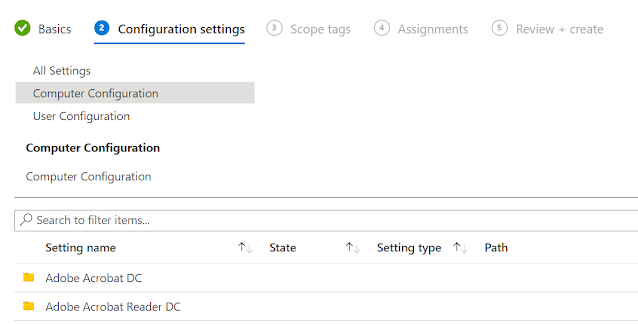
In Windows 10 and 11, the operating system can provide protection from malicious code by isolating certain processes in the PC’s memory using virtualization on supported hardware. This protection runs under Memory Integrity under Core Isolation feature. With Windows 11 22H2, Microsoft made this feature default. However, as of writing this post, Memory Integrity will only turn on new devices by default. For existing devices upgrading to Windows 11 22H2, the feature will need to be managed separately. Memory integrity is also known as Hypervisor-protected Code Integrity (HVCI). Being a device guard feature, it hasn't made to the dedicated security profiles under Endpoint Security Attack Surface Rules in Intune as a standalone policy. Official documentation by Microsoft suggests that it can be enabled as part of Applocker Code Integrity CSP . Alternatively, one can also enable it through the Applocker policy in Application control ASR, if you want to enable Applocker policy as a w