Microsoft Defender Application Guard & Web Content Filtering in Defender for Endpoint - A tale of two cities
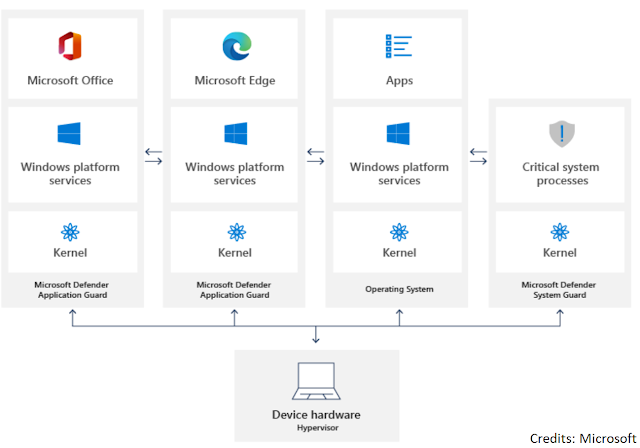
Just a while ago, I blogged on How to enable and configure Web Content Filtering within Microsoft Defender for Endpoint and also on Creating custom Network Indicator rules in Defender for Endpoint . Now as part of a wider implementation for Defender features, I moved on to configuring Application Guard . While the configuration of Application Guard is straight forward, I found out that this feature cannot work along side Web Content Filtering . Why is that? Well to understand this, let's first see what Application Guard is and how does it work. Application Guard For Microsoft Edge, Application Guard helps to isolate untrusted sites that have not been defined in the trusted web sites, cloud resources, and internal networks. Everything else is considered untrusted and sites open in an isolated Hyper-V-enabled container. Similarly, in case of Microsoft Office, Application Guard helps prevents untrusted Word, PowerPoint and Excel files from accessing trusted resources. Here too




