Enable Enhanced Phishing Protection on Windows 11 22H2 using Intune
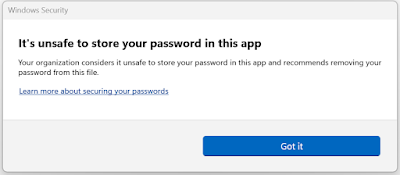
Microsoft recently released next version of Windows 11 known as 22H2. This feature update comes with many new security capabilities and one of such capability is Enhanced Phishing Protection. As part of Microsoft Defender SmartScreen, Enhanced Phishing Protection helps in protecting Microsoft school or work passwords against phishing and unsafe usage on sites and apps. It currently supports the following 3 scenarios: 1. If users type their work or school password on any Chromium browser, into a site deemed malicious by Microsoft Defender SmartScreen, Enhanced Phishing Protection will alert them. It will also prompt them to change their password so attackers can't gain access to their account. 2. Reusing work or school passwords on sites and apps will prompt them to change their password. 3. Storing plaintext passwords in text editors such as Notepad or Office applications like Word, will result in a warning and a recommendation for removing the password from the file. If you are


