Enable Google Chrome browser extensions using Settings Catalog in Intune to support Conditional Access Policies
When I blogged about using settings catalog for Google Chrome browser settings back in March 2022, I knew this is only a start as Google Chrome's admx was now built into Intune. After only a couple of weeks, I now find myself using settings catalog again to configure yet another Google Chrome browser setting which I had been configuring using CSP all this while. The configuration in question is for enabling specific Google Chrome browser extensions in order to support device state based Conditional Access policies.
Enabling Google Chrome Windows Accounts or Office Online extensions
Windows Accounts or Office Online extensions are required if you want Google Chrome browser to support Conditional Access policies where device state is being used as a condition. Note: These extensions may not work with Hybrid Azure AD join scenario and may only work for Azure AD identity.
In this blog, I will configure Windows Accounts extension as an example. Follow the steps below -
1. Navigate to Microsoft Endpoint Manager admin console.
2. Under Devices > Windows > Configuration profiles > Create profile.
3. Under Platform, select Windows 10 & later.
4. Under Profile types, select Templates > Settings Catalog.
5. Give a name.
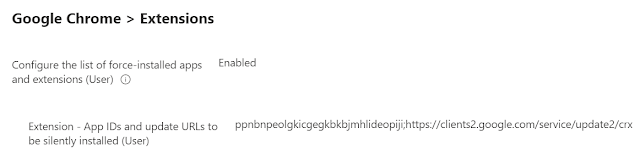
6. Next step is to look for relevant Google Chrome's extension setting. Search for Google Chrome extension and configure the setting as shown below.
This policy supersedes ExtensionInstallBlocklist policy. If a previously force-installed app or extension is removed from this list, Google Chrome automatically uninstalls it. Each list item of the policy is a string that contains an extension ID and, an "update" URL separated by a semicolon (;). By default, the Chrome Web Store's update URL is used.
Syntax is - <32 letter string value>;https://clients2.google.com/service/update2/crx
The extension ids available are -
Windows Accounts - ppnbnpeolgkicgegkbkbjmhlideopiji
Office Online - ndjpnladcallmjemlbaebfadecfhkepb
Conditional Access policy for allowing access from a Compliant Device
If you have a requirement to allow access to corporate resources over browser from compliant devices, then follow the steps below to configure the CA policy.
1. Navigate to Microsoft Endpoint Manager admin console.
2. Go under Devices > Conditional access > New Policy > Create new policy
3. Provide a name.
4. Target the relevant users.
5. Under Cloud apps or actions, select All cloud apps.
6. Under Conditions > Device platforms, select Windows.
7. Under Grant > Grant Access, select Require device to be marked as compliant.
End Result
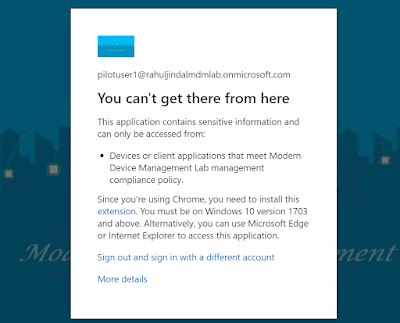
If the extension is missing from Google Chrome, then the user will not be allowed to access the corporate resource using the browser. As an example I am using office.com as the resource.
However, once the extension gets installed silently, the user will be able to access the corporate resources like office.com using organization credentials.
The presence of the extension can be checked by accessing chrome://extensions
Administrators can validate for the enforcement of the right CA policy by accessing the Azure sign-ins.
When the device state is not established because of the missing extension -
When the device state is established because of the presence of the extension -
Compliance state of the policy -














Comments
Post a Comment