Prevent users from running certain programs or applications on Windows endpoints using Intune
When it comes to blocking or preventing users from running an application on Windows devices, one normally uses App locker policy, Windows Defender Application Control and not so new but pretty useful method called Defender Vulnerability management within Microsoft 365 Defender Portal. A recent question on the Tech Community Microsoft forum prompted me to look for all possible alternatives. I started reminiscing over the legacy GPO policies and that is when I stumbled upon the policy Don’t run specified Windows applications located under User Administrative Templates -
The policy setting does come with its own caveat -
"This policy setting only prevents users from running programs that are started by the File Explorer process. It does not prevent users from running programs, such as Task Manager, which are started by the system process or by other processes. Also, if users have access to the command prompt (Cmd.exe), this policy setting does not prevent them from starting programs in the command window even though they would be prevented from doing so using File Explorer"
So if you have to implement this, make sure you are aware of the limitations as stated above. However, if you are ok with restricting access to cmd.exe, then it becomes comparatively easy enough to implement this as oppose to App locker and other alternatives as mentioned before.
So how does one configure this using Intune? Well let's find out -
1. Sign-in to the Microsoft Intune admin Center
2. Browse to Devices – Windows – Configuration Profiles.
3. Click Create Profile.
4. Select Platform as Windows 10 and later.
5. Select Profile as Settings catalog.
6. Provide a Name and hit next.
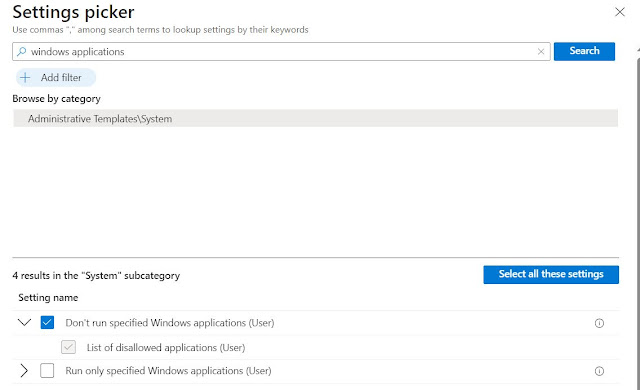
7. Click on Add settings.
8. Search for 'Windows applications' and select 'Don’t run specified Windows applications' as shown below.
9. Add the necessary application process executables and assign to a device or user based group.
End User Experience
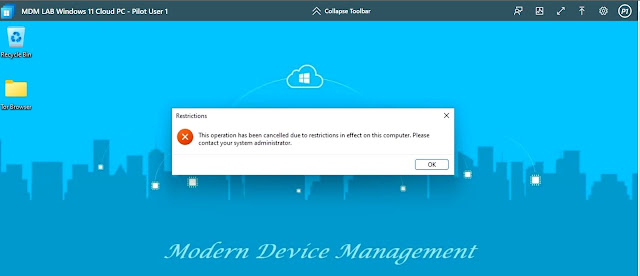
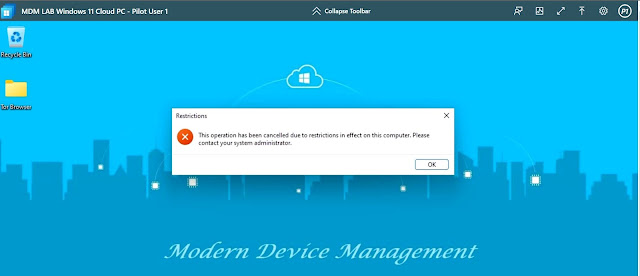
Once the policy is assigned, the setting will come into effect and the user will see the following message on running both cmd.exe and chrome.exe
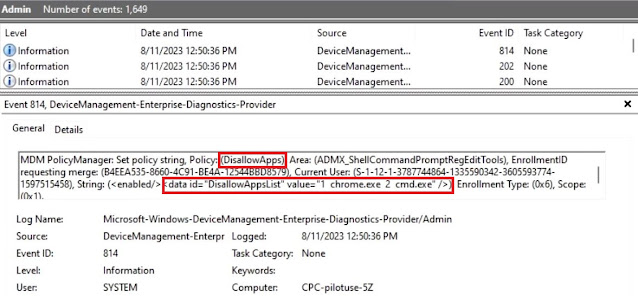
The enforcement of the policy can be validated in eventvwr.
The policy will also create a DisallowRun registry under HKCU.
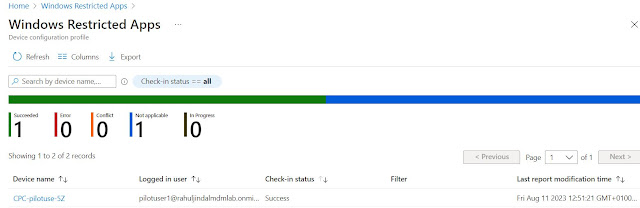
Last but not the least, the compliance of the policy can be tracked in Intune.
Until next time..







Thank you for this great guide, this will be very useful. Do you have any recommendations on an easy rollback incase users are required to use blocked applications in the future?
ReplyDeleteI haven't tested the rollback, but if the CSP allows removal action, then removing the policy may just work. Otherwise, the only other workable option I see is getting rid of the registry through a script.
Deletethanks for the guide!
ReplyDeleteFantastic. Thanks for sharing.
ReplyDeleteIf we rename the file ex. Cmd1.exe it's works even the successful policy
ReplyDeleteThat is because the file name rule doesn't match.
DeleteThis doesnt work with whatsapp
ReplyDeleteHaven't tried it with Whatsapp, but are you seeing any error messages?
DeleteThis article is a gem! I appreciate the detailed research you put into it. It’s refreshing to see such thoroughness!
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteWonderful Article. Thanks for sharing this post
ReplyDeleteMicrosoft Fabric Training
Microsoft Fabric Course
Microsoft Fabric Course in Hyderabad
Microsoft Fabric Online Training Course
Microsoft Fabric Training in Hyderabad
Microsoft Fabric Certification Course
Microsoft Fabric Online Training Institute
Microsoft Fabric Course in Ameerpet
Microsoft Fabric Training in Bangalore
Microsoft Fabric Online Training in India
Microsoft Fabric Training in Chennai
Microsoft Fabric Online Training Course in Bangalore
Wonderful Article. Thanks for sharing this post
ReplyDeleteMicrosoft Fabric Training
Microsoft Fabric Course
Microsoft Fabric Course in Hyderabad
Microsoft Fabric Online Training Course
Microsoft Fabric Training in Hyderabad
Microsoft Fabric Certification Course
Microsoft Fabric Online Training Institute
Microsoft Fabric Course in Ameerpet
Microsoft Fabric Training in Bangalore
Microsoft Fabric Online Training in India
Microsoft Fabric Training in Chennai
Microsoft Fabric Online Training Course in Bangalore
Great blog and you should visit Techlacners a saas consultancy company in Dubai.
ReplyDelete