Enable MFA & SSPR together using combined security information registration in Azure AD
On March 29 2022, Microsoft released MC348869 as a major update in Microsoft 365 Admin message center. The update states that registration for both MFA and SSPR will be combined as a default to give a unified experience to the end user. The change is expected to begin rolling out early October 2022 across all tenants. Note: This change will not impact tenants created after August 2020 or if the tenant is located in China.
From an admin perspective nothing should be required when this change starts to roll out, however, there will be a change in the registration process experience for end users. If this is important to you then you can test this setting right away and make necessary amendments in the end user registration processes.
There are two modes for combined registration -
1. Interrupt mode - It is a wizard-like experience, presented to users when they register or refresh their security info at sign-in.
2. Manage mode - It is part of the user profile and allows users to manage their security info on their own.
In this blog, I will cover both these modes.
Let's first start by enabling combined registration feature in Azure AD
1. Navigate to the Azure portal as a user administrator or global administrator.
2. Go to Azure Active Directory > User settings > Manage user feature settings.
3. Under Users can use the combined security information registration experience, choose to enable for a Selected group of users or for All users.
Next up is to enable SSPR. (Skip this step if already done)
1. Go to Azure Active Directory > Password reset > Manage user feature settings.
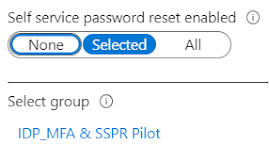
2. Under Self service password reset enabled, choose to enable for a Selected group of users or for All users.
Configure the Authentication methods. (Skip this step if already done)
1. Go to Azure Active Directory > Password reset > Authentication methods.
2. Select the number of methods as 2.
3. Select the necessary methods. In my opinion, select Email, mobile phone at a minimum.
4. Configure the questions if you selected the secret questions as one of the authentication method.
If you want to secure how & when users register for Azure AD Multi-Factor Authentication and self-service password reset, then you do so by using a CA policy. This functionality is particularly helpful if your organization wants to allow registration from a central\trusted location.
To do this, follow the steps below:
1. Navigate to Azure Active Directory > Security > Conditional Access.
2. Select + New policy.
3. Enter a name for this policy.
4. Under Assignments, select Users and groups and choose the users and groups you want this policy to apply to, then select Done.
5. Under Cloud apps or actions, select User actions. Check Register security information, then select Done. Note: At this stage targeted users need to be enabled for combined registration (Demonstrated above).
6. Under Conditions > Locations, configure the following options:
- Configure Yes.
- Include Any location.
- Exclude All trusted locations.
Note: Trusted locations will need to be configured at this stage.
7. Select Done on the Locations window, then select Done on the Conditions window.
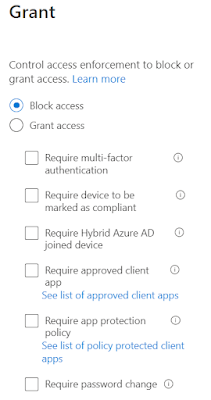
8. Under Access controls > Grant, choose Block access, then Select.
9. Set Enable policy to On. Note: It is a good practice to enable the policy in Report-only mode first.
10. To finalize the policy, select Create.
User Experience & Reporting
When the user tries to register from an unknown or non-trusted location, CA policy will block the registration.
The action will be logged as a failure under Azure sign-ins as well due to the CA policy in place.
When a user does sign-in from a trusted location, then the user's experience will go through the combined security registration wizard (Interrupt mode).
The registration action will get logged in Audit logs in Azure AD confirming that the user registered for all required security info successfully.
Since the action has been performed from a trusted location, the same will reflect in Activity sign-ins.
Now when it comes to Managed mode, user can add their security info themselves by navigating to aka.ms/mysecurityinfo or by navigating to myaccount.microsoft.com. At this point, the user selects Security info in the left pane and from there chooses methods available for registration.
You can also check for SSPR security information by navigating to aka.ms\ssprsetup
Conclusion
The combined registration process is a step closer in making the end user experience more streamlined. It is a good thing that Microsoft is making this a default setting across all tenants. Organizations can decide to wait for the setting to be enabled by default or enable it now and prepare for the change. Until next time..



















Comments
Post a Comment