Winget Apps installation error 0x8A15001B Result:BlockedbyPolicy
I recently encountered an issue while deploying new store apps in a customer's tenant. While there is ample documentation on the new store functionality, I couldn't really find anything specific to my issue and thus it prompted me to write this blog post.
When Microsoft made the announcement that the Microsoft Store for Business and Microsoft Store for Education will be retiring in 2023 and there will be no support for Microsoft Store for Business and Education on Windows 11, it triggered both excitement and concern in the technical community. The new store solution that replaced the existing store functionality is integrated with Intune and has introduced new methods for managing store apps overall.
There are key improvements to the most recent Microsoft Store apps functionality over legacy functionality:
• One can browse and search for store apps within Intune.
• One can install and uninstall with required app deployments.
• One can monitor the installation progress and results for store apps.
• Win32 store apps are supported.
• System context and user context are supported for UWP apps.
Also, it is worth mentioning that the new store supports different types of apps -
Public apps (apps publicly available from an independent software vendor): Use Windows Package Manager via the winget command-line tool to query the single catalog of public apps, through the new Microsoft Store, for apps built by third-party ISV developers regardless of app framework and packaging technology – including Win32, .NET, UWP, Xamarin, Electron, Reactive Native, Java, and PWAs.
Private apps (internal line-of-business apps): Use Windows Package Manager via the winget command-line tool to query your private app repository.
This brings us back to the issue involving error 0x8A15001B that loosely translates to BlockedbyPolicy. By looking at the error one can tell that the issue is caused due to a policy, but the question is which policy. To answer that, let's first look at the pre-requisites for the new store functionality.
1. Client devices must support at least two core processors to successfully install and run Microsoft Store apps.
2. Client devices need to be able to support the Intune Management Extension (IME) to install Microsoft Store apps.
3. Client devices need access to the Microsoft Store and the destination content to install Microsoft Store apps.
In our case, the answer lies in the third pre-requisite that requires access to the Microsoft Store. If the access to the Microsoft Store is blocked by a policy (GPO or otherwise), then following can be the expected behavior when trying to install new store apps.
The user will see the following window when accessing the store app.
The blocking of store policy will create a registry key suggesting the same.
Solution
As I see, there are two possible solutions here.
1. Allow access to public store.
2. Allow access to private store only.
Most organizations will configure option 2 and only allow access to private store. Even with support for private store being removed, one can ensure that installation of arbitrary applications from the Store is restricted without blocking the Intune and Windows Package Manager store integration.
To configure the store policies, you can either do it in GPO, or do it in Intune (Intune is your friend and friends don't let you do Hybrid..😀) using my favorite policy profile i.e settings catalog.
1. Sign-in to the Microsoft Intune admin center.
2. Browse to Devices and look for Configuration>Policies.
3. Click on Create Profile.
4. Select Platform as Windows 10 & later.
5. Select Profile type as Settings catalog.
6. Give a name and configure the following.
7. Assign to a device or user based group.
End Result
Once the policy applies, the registry should update the value of existing RemoveWindowsStore to 0 and add a new registry value RequirePrivateStoreOnly as shown below.
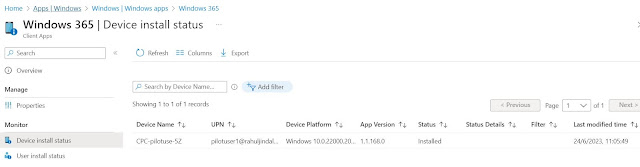
Store App installation will go through without any issues. You can look for the package id captured from Intune.
Compliance for the installation in Intune will update from a failure status to success.
Goodbye old Microsoft Store for business, hello new store experience.












Comments
Post a Comment