Configure Admin approval Workflow for Enterprise Applications to support Intune App Protection Policies
If you manage and protect corporate data on end user devices, then you may have come across situations where enterprise applications may need to be given admin's consent before the policies can be applied. Through this blog, I will be demonstrating a simple admin approval workflow that you can implement in your organizational tenant to allow the use of your Azure AD identity and manage the access permissions against your enterprise apps to protect corporate data when being used by various services. For all intend and purposes, I will be using Intune App Protection Policies as an example when a user tries to access corporate data through Adobe Acrobat Reader on their BYOD.
Let's start by configuring User consent settings
As of writing this blog, currently there are 3 options available for controlling User consent as shown below.
Microsoft recommends to allow user consent for verified publishers, but in my opinion, to ensure complete control of such requests, it is best to only allow an Administrator approve the consent requests. To do this, select the first option.
Next is to configure Admin consent settings
Organizations have a choice to allow users to raise consent requests for the Administrators holding the relevant roles and permissions. While optional, it is highly recommended as this feature gives the flexibility and granular control to the whole admin approval workflow. In my demonstration, I am only allowing Global Administrators to approve the consent requests.
As for the Intune APP, this is what I have setup for BYOD for demonstration purposes.
Time to test
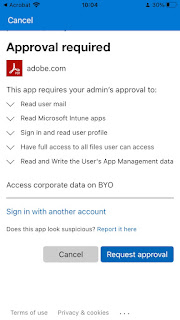
When a user tries to access corporate data through an app that requires Admin consent (Adobe Acrobat Reader in this case), the following workflow will trigger.
1. The user will have to raise a request to the Admin for consent.
2. The user provides justification for the request and clicks on Request approval.
3. The user will see that the request has been raised successfully.
At this stage, the sign-in logs can be verified, which will reflect the same.
4. The Global administrator will receive an email notification that a request has been made. Note: This can be managed through Reviewers under Admin Consent as well.
5. The Global administrator will review the request and grant consent.
6. Once the access is granted in Azure and with the consent permissions in place, when the user tries to authenticate on the application again, the authentication will go through and the application will get registered under Enterprise Applications.
7. The end user will notice that the application has come under Organization's security policies and can proceed to use the application to access corporate data.
8. This will be evident in Intune when checked for APP compliance status.
Final thoughts..
By default, all users are allowed to consent to applications for permissions that don't require administrator consent. For example, by default, a user can consent to allow an app to access their mailbox but can't consent to allow an app unrestricted access to read and write to all files in your organization.
However, to reduce the risk of malicious applications attempting to trick users into granting them access to your organization's data, an Admin approval workflow can be extremely beneficial and should be considered in my honest opinion. Also, in addition to configuring the above settings using Azure Portal, you can use Microsoft Graph Powershell and Microsoft Graph API to configure your tenant.
Until next time..
























Hi, by configuring MAM profiles, on personal devices you are prompted to install (not configure) the company portal, correct?
ReplyDeleteYes, only the installation is required on Android.
DeleteSuch an informative post Thanks for sharing. We are providing the best services click on below links to visit our website.
ReplyDeleteAzure Data Engineer Training Ameerpet
Azure Data Engineer Training Hyderabad
Azure Data Engineer Online Training
Azure Data Engineer Course
Azure Data Engineer Training
Data Engineer Training Hyderabad
Data Engineer Course in Hyderabad
Azure Data Engineer Course Hyderabad
Azure Data Engineer Online Training Course
Such an informative post Thanks for sharing. We are providing the best services click on the links below to visit our website.
ReplyDeleteMicrosoft Dynamics 365 Business Central Training
Dynamics 365 Business Central Training
Dynamics 365 Business Central Online Training
MS Dynamics 365 Business Central Training Hyderabad
Dynamics Business Central Online Training
D365 Business Central Training
D365 Business Central Online Training
Dynamics Business Central Course Hyderabad