Managing & securing web access by using Edge for mobile devices
The importance of mobile security is on the rise and to secure web access, Microsoft recommends using Edge to prevent data leakage, not just on mobile devices but across all device platforms. Being an approved browser for mobile devices, policies can be enforced to protect Office 365 services like Exchange Online, SharePoint Online, the Office portal, and even access to on-premises (intranet) sites via the Azure AD Application Proxy. In addition to this, Edge supports multi-identity which means users can add both work & a personal account, thus allowing complete separation between the two identities. Something which is already offered in other Microsoft mobile apps.
Be it Intune or a third party MDM, managed app configuation can be enforced to pre-load corporate specific settings and also leverage Azure conditional access policies to enforce controls to allow access only using Edge. In this blog, we are going to take a look at what all is involved in putting the configuration together.
Application Configuration using Intune
According to Microsoft -
"App configuration can be delivered either through the mobile device management (MDM) OS channel on enrolled devices (Managed App Configuration channel for iOS or the Android in the Enterprise channel for Android) or through the Intune App Protection Policy (APP) channel. In case of Intune, app configuration delivered through the MDM OS channel is referred to as a Managed Devices App Configuration Policy (ACP); app configuration delivered through the App Protection Policy channel is referred to as a Managed Apps App Configuration Policy."
In this blog, I am using Managed Apps as an example because I am covering both enrolled and BYOD devices as a use case in my tenant. With this configuration, neither the device's enrollment state or how the app is delivered to the device matters.
Following is a complete list of Configuration keys that are currently supported -
In the configuration below, I am using keys that are relevant to my use case. Following is the process -
1. Navigate to Microsoft Endpoint Manager Admin Console.
2. Go under Apps->App configuration policies->Add->Managed Apps.
3. Provide a name.
4. Under Selected apps, add Microsoft Edge for both Android and iOS.
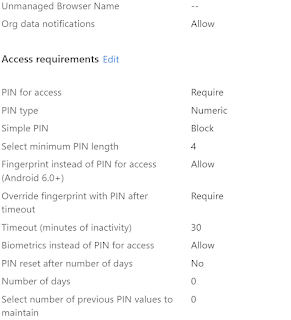
5. Add the necessary configuration settings as shown below -
You have the option to either use configuration keys or use some of the already available configuration settings like setting a homepage, allowing or blocking a list of websites.
6.Assign to a user based group.
Note: If you are deploying APP on an enrolled iOS devices, then depending on your APP settings, you may need to configure IntuneMAMUPN key. I have written a blog covering details on this requirement a while ago. You can read all about it over here.
App Protection policies (APP) using Intune.
APP adds an additional layer of security on MDM enrolled devices and in case of managed apps, an absolute security requirement. I have written a complete blog on the importance of APP and its tier based security framework which you can find here.
For now, let see how you can quickly create an app protection policy in Intune.
1. Navigate to Microsoft Endpoint Manager Admin Console.
2. Go under Apps->App protection policies->Create Policy->Android or iPadOS
3. Provide a name.
4. Configure the settings as shown below -
Android Work Profile
Android BYOD
iOS managed devices
iOS BYOD
5. Assign the policies to the relevant user based groups.
Conditional Access policy for restricting access to Edge
If you are using a subscription that includes Microsoft Intune and Azure Active Directory Premium features, such as conditional access, then at a minimum, you should look at deploying a conditional access policy that only allows connectivity to Edge for iOS and Android, together with Intune app protection policy that ensures the browsing experience is protected.
1. Navigate to Microsoft Endpoint Manager Admin Console.
2. Go under Devices ->Conditional access->New Policy->Create new policy
3. Provide a name.
4. Target the relevant users.
5. Under Cloud apps, select the apps that you want the CA policy to enforce against. Note: Careful if you are selecting All cloud apps. If you are using MDE, then it can break down as MDE is still not part of APP. You can refer to my earlier blogs MDE onboarding for Android & MDE onboarding for iOS in relation to this to get more details.
6. Set the Device platform to mobile devices under conditions.
7. Set the Client apps under conditions.
8. Set Grant access to requiring approved apps and APP.
9. Set the policy On. Note: It is a good practice to set the policy in Report only mode first to assess the impact.
End User Experience & Validation
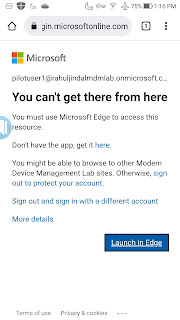
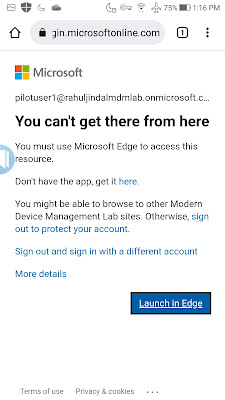
When the user tries to access corporate resource like office.com from an unapproved browser, CA policy will restrict the access and will require the user to use Edge browser instead.
Android
iOS
As for the configuration for Edge, the settings will apply upon next sync.
Android
The homepage is set along with new tab experience.
The bookmarks are created.
URL added under block is not allowed access.
Conclusion
Please note that for configuration scenarios that require device enrollment state, devices need to be enrolled into Intune. Also Edge must be deployed via Intune. For Managed Apps and to leverage app-based conditional access policies, the Microsoft Authenticator app must be installed on iOS devices and Intune Company Portal for Android devices. Once in place, both configuration settings and CA policies should apply seemlessly. It is simply wonderful that Microsoft have provided many options to harden the security on mobile devices. I hope the use case covered in this blog gives some idea on how the configuration can be implemented and what to expect from an end user experience perspective.









































Comments
Post a Comment