Enable Fraud alert in Azure as a counter measure against threats like MFA fatigue
With the recent spate of IT security breaches involving #okta #mfafatigue to name a few, the importance of implementing strong security measures has been put into question once again. Through this blog, I wanted to cover enabling Fraud alert as one of the counter measures, especially against MFA fatigue.
So what is MFA fatigue?
In simple terms, MFA fatigue is tricking users into allowing device access due to overload of push notifications through Authenticator App. There are many ways one can about addressing this. Ideally organizations should consider going password-less by replacing push notifications with phone sign-in to thwart threats like MFA fatigue. In case this is not an option or the organization is not ready to implement it right away, then you can consider implementing fraud alert as a counter measure.
What is a Fraud Alert?
As the name suggests, the fraud alert feature lets users report fraudulent attempts being made to access corporate resources using their credentials. When an unknown and suspicious MFA prompt is received, users can report the fraud attempt by using the Microsoft Authenticator app or through their phone.
There are currently 2 ways to report a fraud:
1. Automatically block users who report fraud - If a user reports fraud, the Azure AD Multi-Factor Authentication attempts for the user account are blocked for 90 days or until an administrator unblocks the account.
2. Code to report fraud during initial greeting - When users receive a phone call to perform multi-factor authentication, they can provide the configured code followed by # key. Default is 0# to report a Fraud and just pressing # allows normal sign-in.
Enable Fraud Alert
Enabling Fraud alert is simple task and can be done in a matter of a couple of steps:
1. Navigate to Azure Active Directory > Security > MFA > Fraud alert.
2. Set Allow users to submit fraud alerts to On.
3. Set Automatically block users who report fraud to On.
4. Set Code to report fraud during initial greeting to 0 or digit of your choice. Note: For this to work, Call phone will need to be enabled as one of the verification method against MFA. I have covered the steps in the blog below to enable it.
4. Select Save.
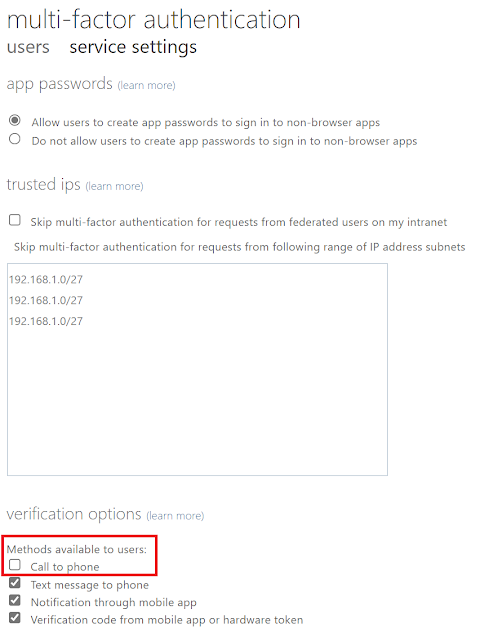
To enable Call phone as a verification method see below:
1. Navigate to Azure Active Directory > Security > MFA > Additional cloud-based MFA settings.
2. Under Verification options, selection Call to phone.
3. Hit Save.
Enable Fraud Alert Notifications
It is advisable to alert Fraud alert notifications for real time reporting. This way security administrators can swing into action immediately.
To configure fraud alert notifications:
1. Navigate to Azure Active Directory > Security > Multi-Factor Authentication > Notifications.
2. Enter the email address to send the notification to.
3. Hit Save.
End User Experience & validation
When users suspects fradulent activity, depending on the method of MFA authentication, they will be presented with the options to report a fraud.
Denying MFA Authenticator App push notification and then reporting a fraud.
With the 'call to phone' MFA authentication option, the user will receive a call with a greeting informing the user about the option of reporting a fraud if they suspect fraudalent activity using their credentials. At this stage, the user can press 0# and report a fraud. I cannot demonstrate it here, but the fraud alerts will be captured in both Azure sign-ins & audit logs.
At this stage, the administrators will revice the Fraud alert mail notification and can also directly take action against the reported account under Blocked accounts under Security -> MFA->Block/unblock users.
Conclusion
In my opinion, it just makes sense to enable and configure Fraud alert regardless of how your MFA is configured. There are other security measure that you can take like enabling password-less, but more on that later. Until next time..















Comments
Post a Comment