Intune - Application Protection Policies for enrolled devices
Recently, I worked on setting up enrollment policies for
Corporate devices in Microsoft Endpoint Manager (MEM aka Intune)
for a customer. As part of the setup, I wanted to apply Application Protection
Policies (APP aka MAM) for enrolled devices to add an additional layer of security and since the devices were
being enrolled in the MDM, I was not bothered about setting up things for BYOD
scenarios.
While the MEM setup and application of the policies is straight
forward for Android, for iOS\iPadOS, there is a bit more involved. I used the Company
Portal enrollment method, so I am going to be focusing on the requirements
for the same in this blog.
The configuration involves 3 things that need to be taken
into consideration –
1. Application configuration policy for iOS\iPadOS.
2. APP for Intune managed devices.
3. APP for unmanaged apps.
Let’s cover the first requirement –
Application configuration policy for iOS\IPadOS
For iOS/iPadOS and for the 'Device type' selection to be
enforced against Intune managed devices, additional app configuration
settings are required. These configurations will communicate to the APP service
that a particular app is managed.
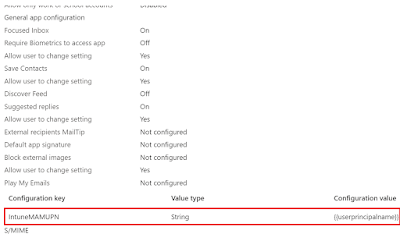
One needs to add the configuration key IntuneMAMUPN
against a managed app to identify the enrolled user account for the sending policy
managed app when transferring data to an iOS managed app. The UPN
configuration works with the app protection policies you deploy from Intune.
Microsoft has documented this requirement pretty well and it can be found here.
After you add the configuration key, the policy should look
something like this.
You will need to do the same for all apps that you want
Intune to manage for APP. Please note, that this is only required for iOS\iPadOS
platform where devices are managed.
Once the above app configuration is place, you can then move
on to the next step for creating the APP policies.
APP for Intune managed devices
It is important to establish the kind of Data Loss
Prevention (DLP) settings you want to configure based on the device
type. You can have one protection policy for unmanaged devices with strict data
loss prevention (DLP) controls, and a separate protection policy for MDM
managed devices, where the DLP controls may be a little more relaxed. In
my case I decided to use same settings for both MDM and MAM APP policies.
Here is what the MDM policy looks like.
APP for Unmanaged Apps
Unlike in Android where a separate Work profile container is
created when enrolling through Company Portal method allowing Intune to
manage all the apps within the Work profile container, iOS\iPadOS does no such
thing if you are enrolling a device using Company Portal under device
enrollment. If a deployed app is already installed before enrollment, then Intune
considers it as an unmanaged app. In other words, for Intune to manage an app,
it must have been installed using the Company Portal.
Therefore, even when a
device is enrolled under MDM, you will need to deploy a separate APP policy to
manage the unmanaged apps for DLP. I created the following policy.
Once MDM & MAM APP policies are created, you can deploy both
to the same User\Device based group.
End Result
Once the policies are applied, you can verify for the status
of the policies in the APP protection status under Apps > Monitor.
You can see how different policies get applied based on the status of the application.
MDM enrolled device with a managed application installed
through Company Portal.
MDM enrolled device with an unmanaged app
Conclusion
While Microsoft has provided some excellent documentation on
the various requirements for APP for both managed and unmanaged apps, they are
easy to miss and can become overwhelming. I hope this blog can help the reader
understand the requirements and the process involved in setting up APP.
Until next time..









Comments
Post a Comment