Managing Software Updates for macOS using Intune with all the shiny bells and whistles!
Every now and then I come across customers seeking advice on managing macOS devices. The most common ask is around keeping them patched and secured which usually tops the list of the requirements. When users install their own updates (instead of admins managing the updates), it can disrupt user productivity and business tasks. Lately, Intune has made huge strides in managing macOS devices as part of cross platform management in general. There are built-in policies in Intune that one can use to manage device updates, configure when devices are updated, and review the device update status.
Currently, there are mainly two ways to manage software updates for macOS using Intune -
1. DDM settings - Recommended on macOS 14.0 and newer devices, DDM is a new way to manage settings allowing installation of a specific update by an enforced deadline. The independent nature of DDM provides an improved user experience, as the device handles the entire software update lifecycle. It prompts users that an update is available and also downloads, prepares the device for the installation, & installs the update.
2. MDM settings - Recommended on macOS 13 and older devices, software update policy can be used to manage when updates are installed, and a settings catalog policy to manage how updates are installed.
While Microsoft recommends using DDM over MDM settings on macOS 14+ devices, if you do end up using both, then there is a precedence order under which the settings will apply.
macOS precedence order:
1. Managed software updates (Settings catalog > Declarative Device Management > Software Update)
2. Update policies (Devices > Update policies for macOS)
3. Software updates (Settings catalog > System Updates > Software Update)
Note: If you configure managed software updates and also have other software update policies assigned, then it's possible the other update policies have no effect.
For all intent and purposes, I went ahead and created both managed and update policies as I wanted to lock down some of the update settings that I didn't want user to tamper with. Let's begin...
Managed Software Updates
DDM settings can be setup using settings catalog for macOS in Intune.
1. Sign-in to the Microsoft Intune admin center
2. Browse to Devices –> Configuration
3. Click Create -> New Policy
4. Select Platform as macOS
5. Select Profile type as Settings catalog
6. Provide a Name and hit next.
7. Click on Add settings.
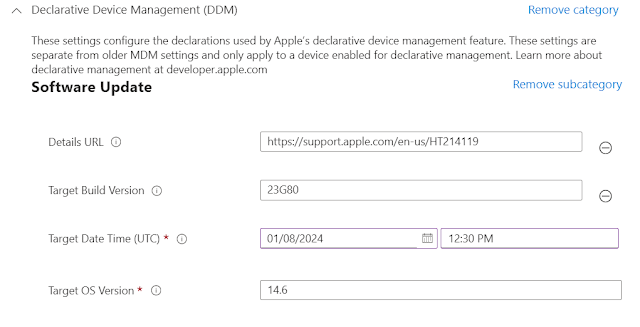
8. Configure the following -
Target Build Version - 23G80 (Note: The system uses the build version for testing during seeding periods. The build version can include a supplemental version identifier, for example, '20A242a'. If the build version isn't consistent with the target OS version specified in the 'TargetOSVersion' key, the target OS version takes precedence.)
Target Date Time (UTC) - 1/8/2024, 12:30:00 (Note: The time specified in the console will be converted to UTC based on the tenant location. In my case it is UTC +1.)
Target OS Version - 14.6 (Note: The time specified in the console will be converted to UTC based on the tenant location.)
Details URL - https://support.apple.com/en-us/HT214119 (Optional)
When you configure managed software updates, you might want to hide updates from users for a specified time period. To hide the updates, we use the same settings catalog policy that configures an update restriction. A restriction period gives you time to test an update before it's available to users. Here is all that I configured -
Software Updates Settings Catalog
As stated earlier under the precedence order, Software Updates settings can be setup using settings catalog for macOS to manage certain features. I configured some, but not all as I want DDM to take over for most part.
1. Sign-in to the Microsoft Intune admin center
2. Browse to Devices –> Configuration
3. Click Create -> New Policy
4. Select Platform as macOS
5. Select Profile type as Settings catalog
6. Provide a Name and hit next.
7. Click on Add settings.
8. Configure the following -
Custom Attribute for macOS for inventory tracking (Optional)
While one can gather patching status through the "macOS update installation failures" device report, I realized that it didn't give me everything related to patching in one place. To address this, I decided to capture the patching details in a custom attribute for macOS. Here is a basic script I put together to gather the details -
#!/bin/sh
#set -x
macOS=$(system_profiler SPInstallHistoryDataType | grep -A 4 "macOS\|Security" | tail -5)
XProtectPayloads=$(system_profiler SPInstallHistoryDataType | grep -A 4 "XProtectPayloads\|Security" | tail -5)
XProtectPlistConfigData=$(system_profiler SPInstallHistoryDataType | grep -A 4 "XProtectPlistConfigData\|Security" | tail -5)
echo "Update History:" $macOS, $XProtectPayloads, $XProtectPlistConfigData
Next is to import it in Intune -
1. Sign-in to the Microsoft Intune admin center
2. Go to Devices -> macOS -> Custom attributes for macOS -> Add.
3. Give a Name and a even a Description if needed.
5. Configure the following settings:
End Result
After the device checks in, the update settings will report as configured, managed and locked down.

Due to the deferral restrictions, the update will not be visible to the user until the deferral period has passed.
Once the deferral period has passed, user will see a prompt that the update is available and scheduled for install based on UTC calculation for the local time against the configured deadline time in the policy.
The update will be visible under General-> Software Updates together with custom details URL as shown below.
Once the update installs at the scheduled time, the device will report targeted OS version.
The custom attribute for macOS should populate the result as well.
Declarative device management is a game changer as it is an update to the existing protocol for device management that can be used in combination with the existing MDM protocol capabilities. Not only it allows the device to asynchronously apply settings and report status back to the MDM solution without constant polling, but also gives the organizations more confidence that devices are being patched and kept in desired state. The fact that a precedence order is established if multiple update settings are enforced, certainly allows more flexibility and options.














Such an informative post Thanks for sharing. We are providing the best services click on the links below to visit our website.
ReplyDeletePower Apps and Power Automate Training
Microsoft Power Apps Online Training
Microsoft Power Apps Course Hyderabad
Power Apps Online Training
Power Apps Training
Power Apps Training Hyderabad-Ameerpet
Power Apps Training Ameerpet
Microsoft Power Platform Online Training
Microsoft Power Automate Training Course
Power Automate Online Training
Very informative content..! It is ingeniously combines deep insights with a fresh perspective, delivering a captivating narrative that challenges conventional thinking and inspires new ideas.
ReplyDeleteNEBOSH Environmental Management