Microsoft Defender for Endpoint for Android Enterprise Personal Profile and Privacy Controls
I recently implemented MDE for Android Work profile devices for a customer and as part of the requirements, the customer wanted to extend Defender management to Personal profile to meet their data protection IT security policies. In this blog, I explore the configuration and cover specifics involving data protection and privacy controls for personal profile in Android Enterprise.
Defender for Endpoint for mobile devices has been around for sometime now. I had covered the details of MDE onboarding for Android devices back in 2022 and it still holds up. While organizations can leverage the MAM scenario to onboard personal devices on MDE, it doesn't cover all the device management capabilities as compared to enrollment into an MDM solution like Intune. To address both data protection and end user privacy requirements of an organization, the Defender management under work profile can also be extended to personal profile. This way organizations can collect the necessary information to help keep Defender for Endpoint for Android secure, up to date, performing as expected and to support the service. Let's see how this can be done..
Pre-requisites
1. Device already enrolled in Intune.
2. Defender App pushed and configured in Work profile.
3. Intune & Defender for Endpoint License.
If you would like to know the details on setting up the pre-requisites then you can head over to one of my earlier blog posts.
Intune App Configuration
There are mainly two ways to configure the relevant app configuration settings. You can either use the JSON or the built-in configuration designer. We are going to use the latter for the simple reason that it is aligned with settings catalog kind of experience and easier to administer.
1. In Microsoft Intune admin center, go to Apps > App configuration policies
2. Click on Add and select Managed Devices.
3. Provide a name and select Platform as Android Enterprise.
4. Under Profile Type, select All Profile Types.
5. Under Targeted app, select Microsoft Defender: Antivirus
6. Add the highlighted permissions and configuration settings for enabling Defender for Personal profile. Note: I have provided other settings since I am using a single policy to manage Defender in both Work and personal profiles.
7. Assign to relevant user or devices groups. I normally assign to all users and filter for relevant devices.
Configuration in Action
Since Intune will not manage the personal profile, the end users will need to carry out the following steps manually.
As the first step, the end user will need to enable the Company portal app. It should already be installed as part of the Intune Work Profile Company Portal enrollment method. Just that it disables in Personal profile post enrollment as the Company Portal in Work profile takes over. Once enabled, the end users just need to open the Company Portal app and does not require a sign-in.
Next step is to install the Defender application from Google Play store in Personal profile.
If the authenticator app is already installed and configured to include the organization's UPN, then it will auto-populate or else the user will need to provide the email id and complete the authentication and register the device.
Once the above steps are complete, the end user will need to give consent to Defender for necessary permissions.
That is it. At this point, the end user can verify what all is accessible by the organization under Privacy settings.
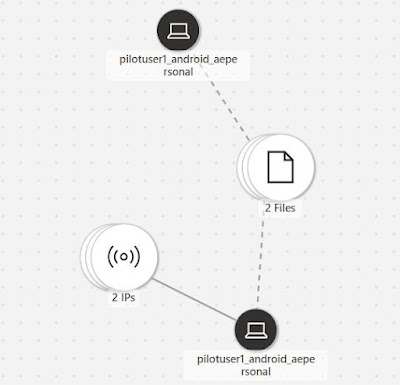
The device will get onboarded as an Android_AEPersonal device in Defender.
Testing for malware and suspicious urls will result in alerts on both end user device under Defender in the personal profile and the Defender portal.
Since the privacy is configured to hide sensitive details like url and app name, these will not show up on the Defender.
However, if the user decides to enable these, then these details will start reporting to the Defender portal.
Additional device events can be accessed using advanced hunting as well. Since the OSFamily reports unknown for Android_AEPersonal devices, I am using device name as condition to fetch the data.
AlertEvidence
| where ServiceSource == "Microsoft Defender for Endpoint"
| extend alertdata=parsejson(AdditionalFields)
| extend LastRemediationState = alertdata.LastRemediationState
| extend OSFamily = alertdata.OSFamily
| where DeviceName contains "android_aepersonal"
Final thoughts..
The best part is that organizations do not need to spend on additional licensing. As long as the devices are enrolled in Intune and onboarded on Defender through Work profile, the same can be extended to the personal profile. While Defender for Endpoint on Android collects information and stores it in the same tenant where you have Defender for Endpoint, what's important to note here is that neither Microsoft or your organization can see data from apps installed on your device, browsing content. The only time your organization will see a website domain, URL would be if attempts are made to visit a site that has been flagged as malicious by Microsoft Defender for Endpoint for containing harmful programs that might steal your personal or financial information. But with privacy controls available in Intune, administrators can hide these details as well.




































Comments
Post a Comment