Why protecting BitLocker Recovery key retrieval is so important..
Majority of organizations will allow end users to retrieve the BitLocker recovery key through self service. While this certainly eases the manageability and cuts down on support calls, the question to ask here is whether it is secure or not. To answer that, let me play out a scenario first.
Let's say a bad actor has got access to a company device and is able to initiate a reboot into advance startup. Now a device that is encrypted with BitLocker protection, will be presented with the screen to enter the recovery key. At this stage one can retrieve the recovery key either through self service portal like https://account.microsoft.com/devices/recoverykey or reach out to service desk. Now what if the attacker has been successful in stealing the credentials of the owner of the device? In the absence of necessary security policies in place, the attacker can retrieve the recovery key from https://account.microsoft.com/devices/recoverykey, or even Entra admin portals by themselves if allowed. Once recovery key is entered, the device can easily be booted into advance startup and the attacker can tamper with the configuration on the device like disabling the Defender components which will not be possible in full OS mode when managed and has Tamper protection enabled. How do I know this? Because I was able to carry out this exact scenario on a test machine and it made me re-evaluate the need for BitLocker key retrieval process in general.
To give some more context, my test device lost connectivity to internet due to rouge Defender FW policies. Not being able to fix this in full OS mode, I circumvented the problem by booting into advanced startup and disabling the Defender components to check if that gets the device back on the internet, which it eventually did and I was then able to fix the issue by applying correct set of policies using Intune.
Now that we have established the context, let's look at the various ways through which one can implement controls around the retrieval of the BitLocker recovery key.
Self-service Recovery
This is the most used method of retrieving the BitLocker recovery key and also the most vulnerable option in my opinion. The ability to retrieve is controlled through a setting under Entra -> Devices -> Device Settings 'Restrict users from recovering the BitLocker key(s) for their owned devices' as shown below -
When set to 'No', the user can access the recovery key.
When set to 'Yes' (Recommended) will then disallow the end user from retrieving the recovery key themselves.
Retrieving through Admin Portal by non-administrators
While Admin portals are meant to be used by administrators assigned with relevant Entra roles, to eliminate the possibility of non-admin users being able to access admin portals, consider implementing a Conditional Access policy to control the access. Here are the steps -
1. Navigate to Microsoft Entra admin center > Protection > Conditional Access.
2. Select Create new policy.
3. Give the policy a name.
4. Under Assignments, select Users or workload identities.
5. Under Include, select All users and exclude all 66 Admin Directory roles. Note: If you manage Entra roles through PIM, then you may have to exclude the administrator user accounts directly otherwise they may not be able to access the PIM portal to activate the Entra role in the first place. Also consider using break-glass accounts to ensure you don't get locked out of the tenant.
6. Under Target resources, select Microsoft Admin Portals.
7. Under Grant controls, select Block access.
Now when a non-admin user tries to access admin portals to retrieve the BitLocker recovery key, their access will be blocked.
Restrictions on retrieval by Administrators
When Microsoft announced last year the ability to create custom roles using permissions for device based objects and managing devices through administrative unit, it extended the possibilities even further for device management at a granular level.
In relation to imposing restrictions on retrieving BitLocker recovery keys by Administrators, we are going to achieve this through a combination of a custom role in Entra with only BitLocker key read permissions, and a dynamic Administrative Unit.
Create Entra ID Security Group
An Entra ID group will need to be created which will support Entra role assignments.
1. Under All groups in Entra admin center, create a new group.
2. Make sure to select 'Yes' against Microsoft Entra roles can be assigned to the group.
Create a custom role
1. To create a custom role using device permissions, go to Roles and admins under Entra, then select New Custom Role and give a name.
2. Select only the BitLocker permissions for this role
Add Administrative Unit
1. Navigate to Admin Units under Entra ID, click Add and give a name.
2. Hit review & create.
3.Once the AU created, open the properties to configure the dynamic device query. You can set it to pull in devices based on specific department or region for management at a granular level. For all intent and purposes, I am just pulling my lab devices.
After the evaluation is done, devices should get added dynamically as members.
Add Assignments for Roles & administrators
1. Assign the custom BitLocker role to the Entra ID group created earlier.
2. Make the assignment type as Eligible.
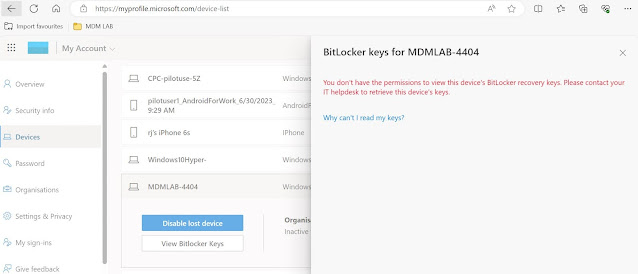
Now when an admin tries to access the admin portal to retrieve the BitLocker keys for the devices targeted under the AU, the information will not be visible unless the custom Entra role is activated.
You can see that BitLocker keys (Preview) is not visible.
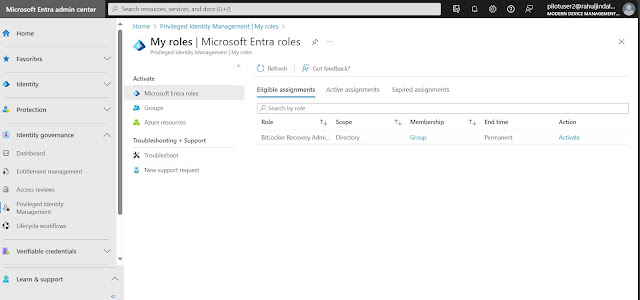
After the Entra role is activated, BitLocker keys will be visible for the device in scope of the AU under the option BitLocker keys (Preview).
Final thoughts..
When it comes to maintaining high security posture, there is no secret formula or a single-solution-fits-all kind of configuration. What organizations should be looking at is how best they can secure the environment by adopting different combinations of settings. While self service retrieval for BitLocker recovery key may sound like an efficient use of service desk calls, it is not ideal and I feel the retrieval process should be confined to only vetted\selected individuals\teams in the organization.
Until next time..























Good post! We are linking to this great post on our website. Keep up the good writing. Thanks for sharing.
ReplyDeleteEasy File Renamer Crack
DVD-Cloner Platinum Crack
Advanced Disk Recovery Crack