Enable Enhanced Phishing Protection on Windows 11 22H2 using Intune
Microsoft recently released next version of Windows 11 known as 22H2. This feature update comes with many new security capabilities and one of such capability is Enhanced Phishing Protection.
As part of Microsoft Defender SmartScreen, Enhanced Phishing Protection helps in protecting Microsoft school or work passwords against phishing and unsafe usage on sites and apps. It currently supports the following 3 scenarios:
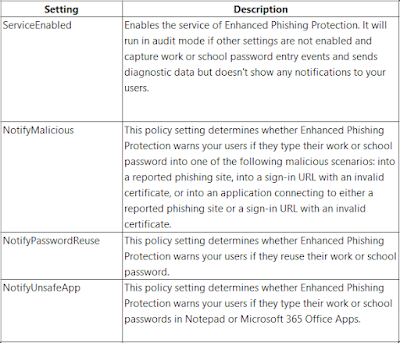
1. If users type their work or school password on any Chromium browser, into a site deemed malicious by Microsoft Defender SmartScreen, Enhanced Phishing Protection will alert them. It will also prompt them to change their password so attackers can't gain access to their account.
2. Reusing work or school passwords on sites and apps will prompt them to change their password.
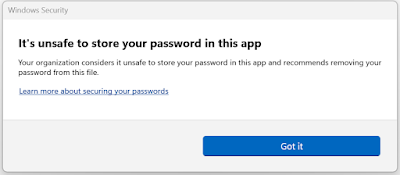
3. Storing plaintext passwords in text editors such as Notepad or Office applications like Word, will result in a warning and a recommendation for removing the password from the file.
If you are an organization that still uses passwords for Windows sign-in or in early stage of password-less journey and an early adopter of Windows 11 22h2, then it is a no brainer to enable this feature.
Luckily Enhanced Phishing Protection works with both Group Policy and mobile device management (MDM) settings. Based on how you set up Enhanced Phishing Protection, you can customize which phishing protection scenarios will show users warning dialogs. Now by default, Enhanced Phishing Protection is deployed in audit mode, preventing notifications to the users for any protection scenarios. However, lets see what all settings are available.
1. Sign-in to the Microsoft Endpoint Manager Admin Center
2. Browse to Devices – Windows – Configuration Profiles
3. Click Create Profile
4. Select Platform as Windows 10 and later
5. Select Profile as Settings catalog
6. Provide a Name and hit next.
7. Click on Add settings.
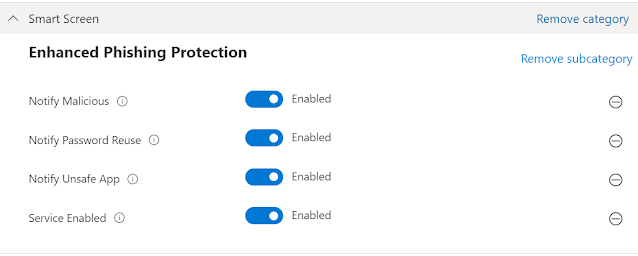
8. Search for 'Phishing' and select the following.
9. Assign to a group of devices or users. (Note: Since this feature is only available with Windows 11 22h2, the settings will only apply to this build)
End Result
Once the policy applies, the user will start seeing relevant warnings.
When user tries to save the Windows logon password in Notepad
When user tries to save the Windows logon password in Word
When user tries to reuse the Windows logon password on a website.
Event Viewer will show events of policy being applied successfully.
Last but not the least, compliance against the settings can be validated in Intune.













Comments
Post a Comment