Creating a single Azure AD Dynamic group containing both Microsoft Intune and Co-managed devices
Working on a project led me to the requirement of targeting some Intune policies on devices that are both Intune and Co-managed. In case of Co-managed, I would normally use Cloud sync to assign the policies on a Microsoft Configuration Manager collection synched with Azure AD and in case of Intune, I would just create a Dynamic Azure AD group containing Autopilot devices or use some basic AAD group attributes in conjunction with device filters in Intune. But this time, I wanted to simplify the grouping and decided to explore the idea of using a single Azure AD dynamic group for all my policy assignments in Intune.
Enter deviceManagementAppid attribute for dynamic grouping of devices in Azure AD.
Microsoft have provided Appids for Intune and Co-managed devices that can be used for dynamic grouping.
For a complete list of supported device attributes, you can refer to the official link over here.
In order to use the Microsoft Intune value ("0000000a-0000-0000-c000-000000000000") and Microsoft Configuration Manager Co-managed value ("54b943f8-d761-4f8d-951e-9cea1846db5a") together, one will need to modify the query manually and outside the default rule builder. Here is what I did when I wanted to create an Azure AD dynamic group containing all Intune and Co-managed Windows 11 devices -
Adjust the AND\OR operators and group the deviceManagementAppid values together as a single condition by adding additional brackets.
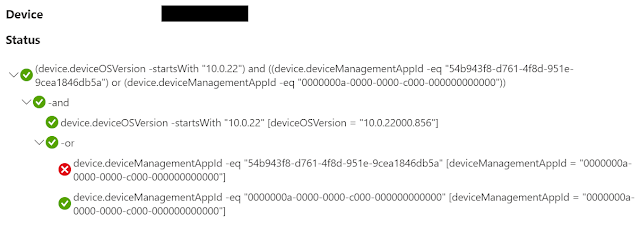
(device.deviceOSVersion -startsWith "10.0.22") and ((device.deviceManagementAppId -eq "54b943f8-d761-4f8d-951e-9cea1846db5a") or (device.deviceManagementAppId -eq "0000000a-0000-0000-c000-000000000000"))
Time to test
When a device is not Windows 11 but managed.
When a device is Windows 11 and Co-managed.







Comments
Post a Comment