Microsoft Defender Application Guard & Web Content Filtering in Defender for Endpoint - A tale of two cities
Just a while ago, I blogged on How to enable and configure Web Content Filtering within Microsoft Defender for Endpoint and also on Creating custom Network Indicator rules in Defender for Endpoint. Now as part of a wider implementation for Defender features, I moved on to configuring Application Guard. While the configuration of Application Guard is straight forward, I found out that this feature cannot work along side Web Content Filtering. Why is that? Well to understand this, let's first see what Application Guard is and how does it work.
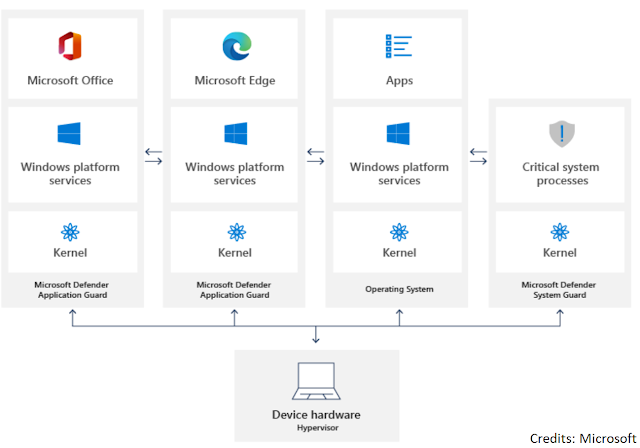
Application Guard
For Microsoft Edge, Application Guard helps to isolate untrusted sites that have not been defined in the trusted web sites, cloud resources, and internal networks. Everything else is considered untrusted and sites open in an isolated Hyper-V-enabled container.
Similarly, in case of Microsoft Office, Application Guard helps prevents untrusted Word, PowerPoint and Excel files from accessing trusted resources. Here too, Application Guard opens untrusted files in an isolated Hyper-V-enabled container.
The isolated Hyper-V container is separate from the host operating system. This container isolation means that if the untrusted site or file turns out to be malicious, the host device is protected, and the attacker can't get to the enterprise data.
To put things in the context of Web Content Filtering, with Application Guard for edge turned on, all untrusted sites get opened in an isolated Hyper-V container, thus whitelisting the URLs in a way. So sites following in the category of gambling, games, pornography, which would normally get blocked through Web Content Filtering rules, also get opened.
While this behavior does make sense, I couldn't find anything in Microsoft's documentation for an official word on this. I posted a question in Microsoft Q&A and also opened a case with MS support to get an official word. Both provided the same response stating that this is by design and that one can use either of the features, but not both together.
Here is a response from MS Support -
But this doesn't mean that you cannot use Application Guard at all. If you want to use Web Content Filtering rules, then you have to ensure that you do not enable Application Guard for Edge, however you do have the option to enable it only for isolated Windows environments which will provide protection for Microsoft 365 Apps. Here are the available settings.
When you open an untrusted file, whether downloaded from the internet or an email attachment from outside your organization based on the configured Application guard network boundaries, you should see an Office splash screen and in menu ribbon indicating that the file is being opened in Application Guard session.
The way the untrusted file is opened in an isolated Hyper-V container and both the OS and your enterprise data stay protected.
I must point out that there are some requirements which must be satisfied before you can start using Application Guard feature. Please refer to the official link to get the details.
Conclusion
It is obviously disappointing to learn that with the current design, Web Content Filtering rules cannot be used together with Microsoft Defender Application Guard. However, at the time of writing this, Web Content Filtering is still in public preview so nothing is of certain unless the feature is moved to GA (General Availability).








Comments
Post a Comment