Microsoft Purview DLP Domain Restrictions for macOS
While scoping for a project for a customer involving the features of Microsoft Purview for Windows devices, it got me thinking about other OS platforms like macOS and what all Purview had to offer. As it turns out, there is a lot. From real-time file inspection across different file types & classification to robust policy protection controls, Microsoft Purview DLP offers a rich set of capabilities. As of writing this blog, here is a complete list of features supported on macOS.
Source: Microsoft
Once devices are onboarded into the Microsoft Purview solutions, the information about what users are doing with sensitive items is made visible in the Purview portal. There is a bit involved in getting the macOS devices onboarded and creating policies in Purview, so let's get started.
What are the pre-requisites?
1. If you are using Intune, then make sure the device is enrolled in Intune.
2. Device is onboarded to Microsoft Defender for Endpoint with a minimum version of 101.95.07.x
3. Prepare the Purview onboarding and configuration xml files. (Covered in the this blog post)
4. E5 or equivalent licenses that include MDE and Purview.
5. Turn on device onboarding in Purview
First and foremost, turn on the onboarding in Purview.
Let's start by capturing the relevant config files -
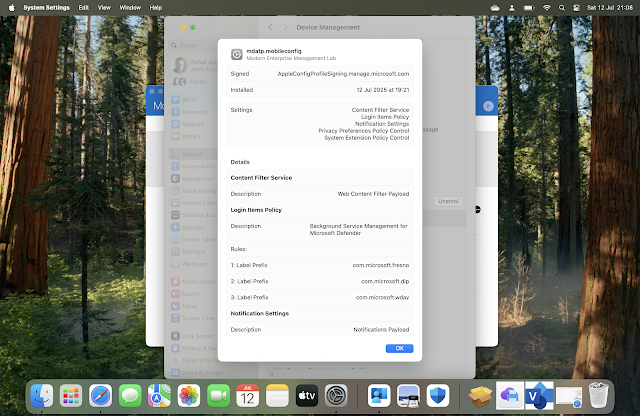
mdatp.mobileconfig
(Note: It is recommended to use as it is bundled with accessibility.mobileconfig, fulldisk.mobileconfig, netfilter.mobileconfig, sysext.mobileconfig)
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0"><dict><key>PayloadContent</key><array><dict><key>PayloadDescription</key><string>Background Service Management for Microsoft Defender</string><key>PayloadDisplayName</key><string>Background Service Management for Microsoft Defender</string><key>PayloadIdentifier</key><string>4DB96276-2310-44C2-AE11-C6E761FB0304.privacy.04102481-C1F1-44F2-B548-E0B554890493</string><key>PayloadType</key><string>com.apple.servicemanagement</string><key>PayloadUUID</key><string>A9BF8FA9-CEA3-42A2-B8C1-E1998B84CBB0</string><key>Rules</key><array><dict><key>RuleType</key><string>LabelPrefix</string><key>RuleValue</key><string>com.microsoft.fresno</string></dict><dict><key>RuleType</key><string>LabelPrefix</string><key>RuleValue</key><string>com.microsoft.dlp</string></dict><dict><key>RuleType</key><string>LabelPrefix</string><key>RuleValue</key><string>com.microsoft.wdav</string></dict></array></dict><dict><key>FilterDataProviderBundleIdentifier</key><string>com.microsoft.wdav.netext</string><key>FilterDataProviderDesignatedRequirement</key><string>identifier "com.microsoft.wdav.netext" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9</string><key>FilterGrade</key><string>inspector</string><key>FilterPackets</key><false/><key>FilterSockets</key><true/><key>FilterType</key><string>Plugin</string><key>PayloadDisplayName</key><string>Web Content Filter Payload</string><key>PayloadIdentifier</key><string>283F4BF0-788A-4435-9B62-3E00896358D7</string><key>PayloadOrganization</key><string>JAMF Software</string><key>PayloadType</key><string>com.apple.webcontent-filter</string><key>PayloadUUID</key><string>283F4BF0-788A-4435-9B62-3E00896358D7</string><key>PayloadVersion</key><integer>1</integer><key>PluginBundleID</key><string>com.microsoft.wdav</string><key>UserDefinedName</key><string>Microsoft Defender Content Filter</string></dict><dict><key>NotificationSettings</key><array><dict><key>AlertType</key><integer>1</integer><key>BadgesEnabled</key><true/><key>BundleIdentifier</key><string>com.microsoft.autoupdate2</string><key>CriticalAlertEnabled</key><false/><key>NotificationsEnabled</key><true/><key>ShowInLockScreen</key><false/><key>ShowInNotificationCenter</key><true/><key>SoundsEnabled</key><true/></dict><dict><key>AlertType</key><integer>1</integer><key>BadgesEnabled</key><true/><key>BundleIdentifier</key><string>com.microsoft.wdav.tray</string><key>CriticalAlertEnabled</key><false/><key>NotificationsEnabled</key><true/><key>ShowInLockScreen</key><false/><key>ShowInNotificationCenter</key><true/><key>SoundsEnabled</key><true/></dict></array><key>PayloadDisplayName</key><string>Notifications Payload</string><key>PayloadIdentifier</key><string>05BF7221-2470-477D-99B3-1729B1932BDB</string><key>PayloadOrganization</key><string>Microsoft Corporation</string><key>PayloadType</key><string>com.apple.notificationsettings</string><key>PayloadUUID</key><string>05BF7221-2470-477D-99B3-1729B1932BDB</string><key>PayloadVersion</key><integer>1</integer></dict><dict><key>AllowUserOverrides</key><true/><key>AllowedSystemExtensions</key><dict><key>UBF8T346G9</key><array><string>com.microsoft.wdav.epsext</string><string>com.microsoft.wdav.netext</string></array></dict><key>PayloadDescription</key><string></string><key>PayloadDisplayName</key><string>System Extensions</string><key>PayloadEnabled</key><true/><key>PayloadIdentifier</key><string>605B85D6-5CE9-49C9-A10F-6B12B4D0B84E</string><key>PayloadOrganization</key><string>Microsoft Corporation</string><key>PayloadType</key><string>com.apple.system-extension-policy</string><key>PayloadUUID</key><string>605B85D6-5CE9-49C9-A10F-6B12B4D0B84E</string><key>PayloadVersion</key><integer>1</integer></dict><dict><key>PayloadDescription</key><string></string><key>PayloadDisplayName</key><string>Privacy Preferences Policy Control</string><key>PayloadEnabled</key><true/><key>PayloadIdentifier</key><string>E23CA4BE-65BA-4685-89D6-041F82994606</string><key>PayloadOrganization</key><string>Microsoft Corporation</string><key>PayloadType</key><string>com.apple.TCC.configuration-profile-policy</string><key>PayloadUUID</key><string>E23CA4BE-65BA-4685-89D6-041F82994606</string><key>PayloadVersion</key><integer>1</integer><key>Services</key><dict><key>Accessibility</key><array><dict><key>Allowed</key><integer>1</integer><key>CodeRequirement</key><string>identifier "com.microsoft.dlp.daemon" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9</string><key>Identifier</key><string>com.microsoft.dlp.daemon</string><key>IdentifierType</key><string>bundleID</string><key>StaticCode</key><integer>0</integer></dict></array><key>SystemPolicyAllFiles</key><array><dict><key>Allowed</key><integer>1</integer><key>CodeRequirement</key><string>identifier "com.microsoft.wdav" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9</string><key>Identifier</key><string>com.microsoft.wdav</string><key>IdentifierType</key><string>bundleID</string><key>StaticCode</key><integer>0</integer></dict><dict><key>Allowed</key><integer>1</integer><key>CodeRequirement</key><string>identifier "com.microsoft.wdav.epsext" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9</string><key>Identifier</key><string>com.microsoft.wdav.epsext</string><key>IdentifierType</key><string>bundleID</string><key>StaticCode</key><integer>0</integer></dict><dict><key>Allowed</key><integer>1</integer><key>CodeRequirement</key><string>identifier "com.microsoft.dlp.daemon" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9</string><key>Identifier</key><string>com.microsoft.dlp.daemon</string><key>IdentifierType</key><string>bundleID</string><key>StaticCode</key><integer>0</integer></dict></array></dict></dict></array><key>PayloadDescription</key><string></string><key>PayloadDisplayName</key><string>Defender onboarding settings</string><key>PayloadEnabled</key><true/><key>PayloadIdentifier</key><string>23FE3F82-71F0-11EF-89EE-26DE397E1932</string><key>PayloadOrganization</key><string>Microsoft Corporation</string><key>PayloadRemovalDisallowed</key><true/><key>PayloadScope</key><string>System</string><key>PayloadType</key><string>Configuration</string><key>PayloadUUID</key><string>23FE3F82-71F0-11EF-89EE-26DE397E1932</string><key>PayloadVersion</key><integer>1</integer></dict></plist>
com.microsoft.wdav.mobileconfig
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1">
<dict>
<key>PayloadUUID</key>
<string>C4E6A782-0C8D-44AB-A025-EB893987A295</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadOrganization</key>
<string>Microsoft</string>
<key>PayloadIdentifier</key>
<string>com.microsoft.wdav</string>
<key>PayloadDisplayName</key>
<string>Microsoft Defender for Endpoint settings</string>
<key>PayloadDescription</key>
<string>Microsoft Defender for Endpoint configuration settings</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadUUID</key>
<string>99DBC2BC-3B3A-46A2-A413-C8F9BB9A7295</string>
<key>PayloadType</key>
<string>com.microsoft.wdav</string>
<key>PayloadOrganization</key>
<string>Microsoft</string>
<key>PayloadIdentifier</key>
<string>com.microsoft.wdav</string>
<key>PayloadDisplayName</key>
<string>Microsoft Defender for Endpoint configuration settings</string>
<key>PayloadDescription</key>
<string/>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadEnabled</key>
<true/>
<key>antivirusEngine</key>
<dict>
<key>passiveMode</key>
<true/>
</dict>
<key>cloudService</key>
<dict>
<key>diagnosticLevel</key>
<string>optional</string>
</dict>
<key>features</key>
<dict>
<key>dataLossPrevention</key>
<string>enabled</string>
</dict>
</dict>
</array>
</dict>
</plist>
Import .mobileconfig files in Intune.
1. Sign-in to the Microsoft Intune admin center
2. Browse to Devices –> Configuration
3. Click Create -> New Policy
4. Select Platform as macOS
5. Select Profile type as Templates > Custom
6. Provide a Name and hit next.
7. Configure similar to as shown below & pull the .mobileconfig files created earlier in this blog post (Note: You will need two profiles. One for each .mobileconfigs).
8. Assign to user or device based group.
Creating a Sensitivity Label
Sensitivity label is required for implementing all Microsoft Purview Information Protection solutions.
When you use Data Security Posture Management for AI, you can activate some default sensitivity labels as shown below -
You can create a sensitivity label manually as well by following the steps below -
1. Navigate to Microsoft Purview admin portal.
2. Under Solutions, click Information Protection.
3. Go to Sensitivity labels > Create a label.
4. Give a display name and set the label priority as needed.
5. Define the scope as needed. I have selected Files & other data assets, Emails and Meetings. (Note: If you wish to configure privacy and access control for Teams and SharePoint sites through Groups & sites, then additional steps may be needed.)
6. Choose the protection settings for the types of items as shown below. You can apply custom content marking if needed. I decided to leave it out.
7. Apply the access control permissions as necessary. You can use built-in permission categories or create your own. For example, you can assign viewer level permissions to a set of users only.
8. You have the option to configure Auto-labeling for files and emails based on certain conditions. I have left it not configured as default.
9. Leave the defaults for groups and sites.
10. Review and finish the creation of the sensitivity label. After it is created, you can always edit it.
Sensitivity Label publishing
Now that a sensitivity label has been created, it still needs to be published to your users in the organization. Until you publish your labels, they won't be available to select in apps or for services.
1. Sign in to the Microsoft Purview portal > Solutions > Information Protection > Publishing policies.
2. On the Label policies page, select Publish label to start the Create policy configuration.
3. On the Choose sensitivity labels to publish page, select the Choose sensitivity labels to publish link. Select the labels that you want to make available in apps and to services, and then select Add.
4. Select the sensitivity labels to publish.
5. If you use Admin units in your tenant, then you can configure AU to further scope the users or groups.
6. Publish it to the relevant set of users and groups. I have selected all users and groups in my demo tenant, but I'll advice to publish to a set of users for testing first.
7. Configure the policy settings as shown below. You can enable label for Fabric, Power BI and provide a link to a custom help page should you need it.
8. Give a name to the policy and finish the policy creation process. (Note: It can take up to 24 hours for the policy to be published and made available to all the intended users and groups. Changes and modifications can take anywhere between 1-6 hours)
9. You can also edit the policy after it is created.
Creating the DLP Policies
For all intent and purposes, I am focusing on domain restrictions for allowing uploading of corporate data to a list allowed domains only. This way users will be blocked from uploading corporate data to non listed domains like personal emails.
1. Navigate to Microsoft Purview admin portal.
2. Under Settings > Data Loss Prevention, click on Browser and domain restrictions to sensitive data and then Domain services to add a list of allowed domains. In my scenario, I am only adding SharePoint and One Drive for Business URLs as shown below -
3. Under Data Loss Prevention, click on Policies and hit Create Policy.
4. Choose the type of data to be covered under the policy. I selected 'Data stored in connected sources' to protect data against M365 and managed devices.
5. Select a pre-defined template to pull in relevant DLP settings or select a custom to create your own. I need to configure selective controls therefore I selected custom.
6. Give a relevant name and hit next. Assign admin units if you need to scope it further for users and groups. I went with default values here.
7. Select the locations that you want the policy to configure against. Since I am creating a custom policy for DLP controls, I had to select the supported locations as shown below -
8. This is where we start creating conditions. If you have a similar use case, then just configure the settings as shown below. Select all the required sensitivity labels.
9. Then set the value as 'Block' against 'Upload to a restricted cloud service domain or access from unwanted browsers' under 'Service domain and browser activities'.
10. Configure 'Block' against the activities as shown below.
11. Select the user notifications as necessary.
12. Set the policy mode to enable. You also have the option to put the policy in simulation mode, however, this didn't give me in any relevant data in my demo tenant at least. However, I'll encourage you to use the feature before turning on the policy.
End Result
After the macOS device has received the configuration settings for DLP from Intune, the feature will report as enabled and the profiles will be configured.
The sensitivity label will be assigned automatically based on the publishing settings for the documents and emails.
When a user tries to upload document attached with sensitivity label to a restricted domain like personal email, the upload will be blocked and the user will be notified.
Lastly, the Intune profiles will report successful compliance status.
Final thoughts..
In Microsoft Purview, DLP policy evaluation of sensitive items occurs centrally, so there's no time lag for policies and policy updates to be distributed to individual devices. In my honest opinion, macOS support for Endpoint DLP has significantly matured. While there are still limitations in form of VPN or network share exclusions not being supported and the lack of a full file evidence capture, everything else is in near parity with Windows for file-based controls, activity restrictions, classification, and paste-to-browser enforcement.













































Comments
Post a Comment