'Device States' in Conditional Access for both Corporate and Personal Intune managed devices - A retrospect
Source:Microsoft
With the help of Microsoft Intune, organizations can use the device states returned from the enrolled devices to Entra ID to identify whether these devices meet specific policy compliance requirements and accordingly enforce controls to grant or block access to corporate resources. With device states, once the user has successfully authenticated, a Primary Refresh Token (PRT) containing both user and device claims is issued. With conditional access policies requiring either a device-based control or a multifactor authentication control in place, the policy requirement can be met through its device state using PRT without attempting MFA. This is because when a PRT requests access to an application, its device, session, and MFA claims are trusted by Microsoft Entra ID. The PRT is valid for 14 days and is continuously renewed as long as the user actively uses the device, providing users a resilient experience.
With the currently available device states, Microsoft recommends the following to be implemented aligning with Zero trust security framework -
1. Enable Microsoft Entra hybrid joined and Microsoft Entra join for company-owned Windows devices and require that they be joined, or be registered at the very least.
2. Standardize user browser access to use either Microsoft Edge or Google Chrome with the Microsoft Single Sign On extension that enable seamless SSO to web applications using the PRT.
3. For personal or company-owned iOS and Android devices, deploy the Microsoft Authenticator App. In addition to MFA and password-less sign-in capabilities, the Microsoft Authenticator app enables single sign-on across native applications through brokered authentication with fewer authentication prompts for end users.
4. For personal or company-owned iOS and Android devices, use mobile application management to securely access company resources with fewer authentication requests.
5. For macOS devices, use the Microsoft Enterprise SSO plug-in for Apple devices (preview) to register the device and provide SSO across browser and native Microsoft Entra applications.
I recently had a requirement of segregating conditional access policies for Intune managed corporate and personal devices. While addressing this requirement and aligning with the necessity of building resiliency with device states, I revisited Conditional Access and decided to leverage device filters to achieve this.
The filter for devices condition in Conditional Access evaluates policy based on device attributes of a registered device in Microsoft Entra ID. These can used for targeting or excluding specific devices by using attributes available within the device filters. However and as at the time of writing this blog, Microsoft Entra ID uses device authentication to evaluate device filter rules. Therefore for a device that is unregistered with Microsoft Entra ID, all device properties are considered as null values and the device attributes cannot be determined since the device does not exist in the directory.
Attributes currently available -
Creating the Conditional Access policies using device filters and device states for Corporate and Personal devices
1. Sign in to the Microsoft Entra admin center.
2. Browse to Protection > Conditional Access > Policies and select New policy.
3. Give your policy a name.
4. Under Assignments, select Users or workload identities.
5. Under Target resources > Cloud apps > Include > Select All Cloud apps, or as required.
6. Under Conditions> Filter for devices> Include> Use deviceOwnership and set the value as shown below.
For Corporate\Company devices
For Personal devices
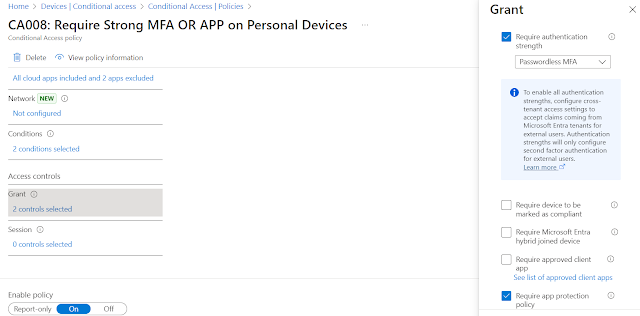
7. Under Access controls > Grant, select Grant access as shown below.
For Corporate devices, I am checking for the compliance state.
For Personal devices, I am checking for MFA OR App Protection Policy (APP)
8. Confirm your settings and set Enable policy to On.
9. Select Create to create to enable your policy.
Policies in action
I tested the policies on both corporate and personal devices to see if the relevant conditional access policies applied or not.
Corporate device Entra ID - 03abbb47-7fa9-481c-a011-fc0b15a9a212
CA007: Require Compliant for Corporate Devices - Applied
CA008: Require Strong MFA OR APP on Personal Devices - Not Applied
Personal device Entra ID - f0c64a30-e6a2-4a93-a3a7-84d8e1796d75
CA007: Require Compliant for Corporate Devices - Not Applied
CA008: Require Strong MFA OR APP on Personal Devices - Applied
That's it for now. Thank you for reading. Hope the above scenario helped in understanding on building resilience with device states for both corporate and personal devices. Until next time..














A better filter for personal devices is "device.deviceOwnership -ne "Company"", that way you'll catch unregistered devices as well (if that's your goal of course).
ReplyDeleteThanks for sharing. Yes, certainly an option if the end goal is to catch all unregistered devices like you said. However, in this blog the use case is for managed devices only.
Delete