Secure Home folders in macOS using Intune
If you have onboarded your macOS devices onto Defender for Endpoint, then more often than not, you will see the vulnerability recommendation flagging for 'Secure Home folders in macOS' affecting the secure score.
The potential risk here being is that allowing all users to view the top level of all networked user's home folder may not be desirable since it may lead to the revelation of sensitive information. This is because by default macOS allows all valid users into the top level of every networked user's home folder, with the ability to view the folder content and this can be a security risk.
The remediation steps involves running commands in Terminal for each user account with a local home folder to modify the permissions. In my honest opinion, if the macOS devices are meant for single user use, then this recommendation may not really apply. But in case of multiple users, it is a whole different story. Regardless of the device use, if you are looking to address this recommendation to improve the secure score, then please keeping reading. :-)
While the recommendation requires modifying permissions for each user account to Read & Write, I noticed during my testing that even after configuring the desired permissions against the user account, the recommendation didn't go away. This is when I realized that permissions needed to be modified for the Shared folder located under Users/Shared as well. Honestly, I am not sure why Microsoft requires setting the permissions for the Shared folder as it is normally required to be accessible by all users, but for some reason the recommendation doesn't like it being set with default permissions. What makes this super weird is that, hardening the permissions of the Shared folder is not flagged in the recommendation steps either. Be it as it may, the permissions need to be modified, so let's get into it.
I prepared a bash script to modify the permissions which will allow execution against both the current user and Shared folder.
#!/bin/bash
currentuser=$(/bin/ls -la /dev/console | /usr/bin/cut -d ' ' -f 4)
sudo chmod -R og-rw /Users/$currentuser
sudo chmod -R og-rw /Users/Shared
Let's import it in Intune.
1. Navigate to Microsoft Intune admin center.
2. Go to Devices>Scripts & remediations>Platform scripts>Add>macOS.
3. Give a name & description.
4. Select the .sh script and set the execution settings as shown below or matching your requirements.
5. Assign script to group of devices or users.
Validation Results
The permissions will modify on the targeted macOS device for the targeted folders.
The device timeline on the Defender portal captures the actions and the events reflecting the modification of the permissions. You can see the script pulled the folder of the currently logged on user.
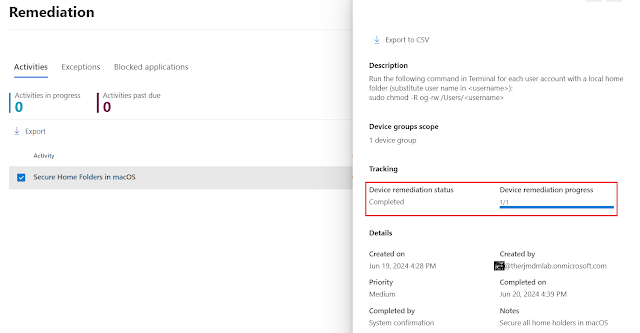
And lastly, the recommendation will update the statistics around remediated devices.
You can create a remediation task against the remediation and that should update as well.
Final thoughts..
I will still like to do things for macOS the same way as one is able to do for Windows in Intune. Using built-in policies is my preferred way, but in absence of that you have to make use of what is available to you. Luckily bash scripts are super useful and surely a .sh script did the trick this time as well. It will be nice if the recommendation was clearer on setting the permissions of the Shared folder, but it is what it is. Speaking of which, if your users have a business requirement for using the Shared folder then maybe it will be a good idea to set the permissions to allow Execute as well.
You can do so by running the following - sudo chmod -R og-rwx /Users/Shared
It should then reflect as below -
That's it for now. Until next time..












Question. To get the remediation points, does every account on the mac need to have the Home Folder secured? Let's say we have the main user account, an it admin account, and sometimes a third account. Your script would only secure the current user correct?
ReplyDelete