Configuring Intune RBAC just-in-time admin access with Entra ID PIM for Groups & Conditional Access
For a long time Role-based access control (RBAC) has been the method of choice for managing access to organization's resources by using built-in Intune roles. However, there was no way to enforce just-in-time like access control against these roles. This changed earlier in the year 2023, when Microsoft released Privileged Identity Management (PIM) for Groups which allowed creating a just-in-time (JIT) policy to support a wide range of roles such as Microsoft Entra roles, Azure resource roles, Microsoft Intune and non-Microsoft application roles and services.
As of writing this blog, this feature together with PIM integration with Conditional Access went into GA which has now enabled organizations to enforce specific requirements for PIM role activations, thus enhancing the overall security posture.
In this blog post, I explore these methods on how to give users just-in-time privileged access to Intune RBAC by using PIM for Groups and leveraging CA by enforcing additional security checks in form of MFA.
The scenario involves elevating permissions of a Read Only Operator to Cloud PC Administrator using Intune RBAC, PIM for Groups and CA.
Creating the groups in Entra ID
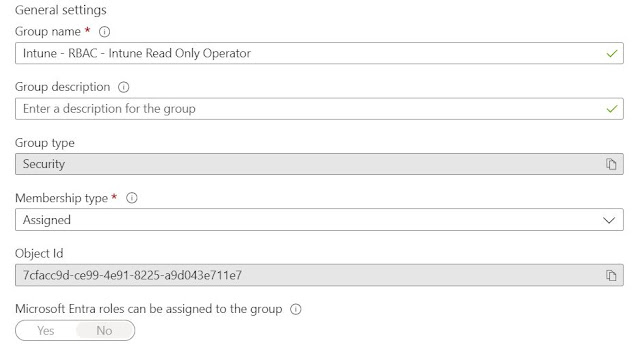
- Create a standard group with assigned membership. Note - You can use an existing group as well.
Intune - RBAC - Intune Read Only Operator
- Create the second group assigned as role-assignable or non-role-assignable. A role-assignable group is one that can be assigned to a role in Azure AD. Such a group can only be managed by Global Administrator, Privileged Role Administrator, or the group Owner which will help in preventing an admin from elevating to a higher privileged role without going through a request and approval procedure.
- No need to add members in this group as it will be used in PIM for groups to implement JIT.
Configure the PIM for Groups in Entra ID
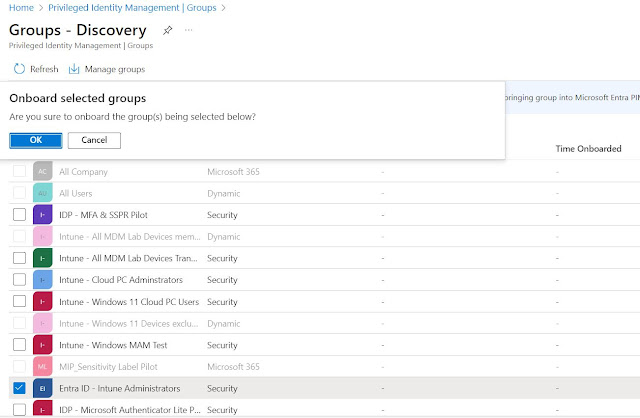
- Navigate to Microsoft Entra admin center > Privileged Identity Management > Groups
- Click on Discover Groups, select & onboard the second group Entra ID - Intune Administrators
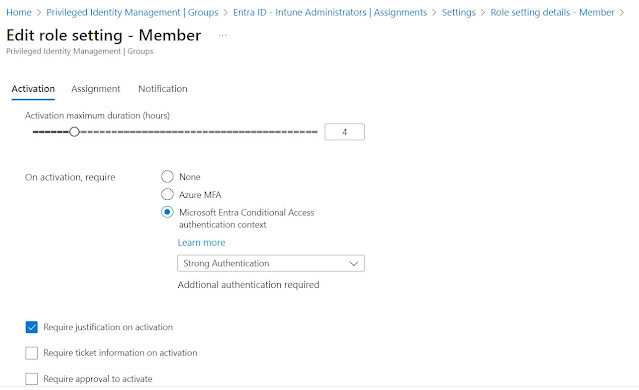
- Select the onboarded group, and under Manage, select Assignments to add a new assignment.
- In the Intune admin center, navigate to Tenant administration > Roles.
- Select the desired least privilege role. In this example, I chose Read Only Operator.
- In the Role, go to Assignments and assign the first group was created i.e. Intune - RBAC - Intune Read Only Operator
- Select the necessary scope groups and save.
Policies in Action
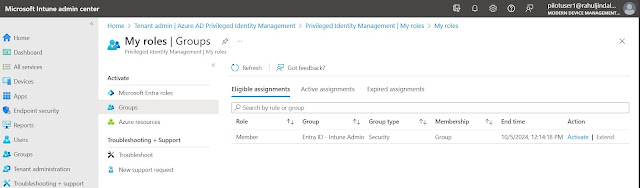
After the role assignment settings are completed, the members of the least-privilege group (Intune - RBAC - Intune Read Only Operator) will be able to request elevated privileges by requesting to be temporarily added to the managed group (Entra ID - Intune Administrators).
Member of Intune - RBAC - Intune Read Only Operator group signs in and has read only permissions.
The user requests for elevation by navigating to Intune admin center > Tenant administration > Azure AD Privileged Identity Management > My roles > Groups
Final thoughts..
Least-Privilege Administrative Models are security best practices where users only have the access they need to perform a given task. This helps prevent unauthorized or accidental changes, data breaches, and compliance violations. Part of Microsoft Entra ID Governance and Microsoft Entra ID P2, you can now further simplify least privilege access by enabling just-in-time access for all resources that support security group or Microsoft 365 group assignments.




















Comments
Post a Comment