Windows LAPS with Microsoft Entra (Azure AD) and Microsoft Intune
As of writing this blog, Microsoft have released Windows LAPS for both Azure AD joined and hybrid Azure AD joined devices. An official Cloud LAPS solution has been long awaited and it is finally here. While still in Public preview, it is a good time to test the feature. I tested the solution in my tenant and captured the relevant bits. Check it out.
First of all, lets see what the current requirements are -
Supported Azure Regions -
-Azure Global
-Azure Government
-Azure China 21Vianet
Operating system updates that are currently needed -
This feature is now available on the following Windows OS platforms with the specified update or later installed:
-Windows 11 22H2 - April 11 2023 Update
-Windows 11 21H2 - April 11 2023 Update
-Windows 10 20H2, 21H2 and 22H2 - April 11 2023 Update
-Windows Server 2022 - April 11 2023 Update
-Windows Server 2019 - April 11 2023 Update
Device identities that are supported -
- Azure AD joined
- hybrid Azure AD joined devices only.
Note: Azure AD registered devices aren't supported.
License requirements -
LAPS is available to all customers with Azure AD Free or higher licenses. Other related features like administrative units, custom roles, Conditional Access, and Intune have other licensing requirements.
Required roles or permission -
Other than the built-in Azure AD roles of Cloud Device Administrator, Intune Administrator, and Global Administrator that are granted device.LocalCredentials.Read.All, you can use Azure AD custom roles or administrative units to authorize local administrator password recovery.
Turn on Windows LAPS in the Tenant
1. Navigate to Entra Admin Center and select Devices.
2. Under Device settings, enable Azure AD Local Administrator Password Solution (LAPS)
Client-side policies via Microsoft Intune
1. Sign-in to Microsoft Intune Admin Center Portal.
2. Browse to Endpoint Security – Account Protection – Create a Policy
3. Select Platform as Windows 10 and later.
4. Select Local Administrator Password Solution (LAPS) as Profile Type and then hit Create.
5. File the relevant fields like Name, Description and click Next.
6. Configure the settings as shown below.
Note: You can use a custom Local admin account, but you will need to create it first outside this process. If you don't use a custom local admin account, then the default local admin account will be used. If you want to know how to create a local admin account, then feel free to visit on of my earlier posts.
Conditional Access policy on directory roles for password recovery (Optional)
Conditional Access policies can be used to protect access to recover local administrator passwords. This can be scoped against the built-in roles like Cloud Device Administrator, Intune Administrator, and Global Administrator.
There are multiple ways to create a CA policy for enforcing MFA against Admin roles. The easiest way is to use the built-in templates.
1. Access Conditional Access through Azure AD > Security > Conditional Access or Microsoft Intune Admin Portal > Devices > Conditional Access menu.
2. Click New policy from Template option and select Require multifactor authentication for Admins.
3. Give a name, review the settings and hit create.
4. Currently the template does not include Cloud Device Administrator and Intune Administrator as the roles, so add them explicitly.
Time to test
If you are working with a custom local admin account, then make sure it is created first. If you are using the built-in local admin account then make sure it is enabled. In my case, I created a custom local admin account and verified for the same.
Next, let's confirm whether the Windows LAPS client side policies assignment from Intune is reporting compliant or not.
So far so good. Next step is to verify the LAPS events in event viewer.
Event id 10022 - LAPS policy configuration
Event id 10010 - LAPS password backup to AAD confirmation
Event id 10015 - Policy evaluation and enforcement. In this case the existing LAPS password that I set for testing was found to be non-compliant and needed to be updated as per Password complexity policy.
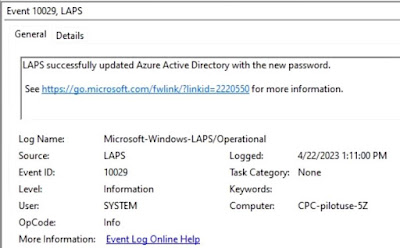
Event id 10029 - LAPS confirmation of updating of the password in AAD.
Event id 10020 - Event id 10029 - LAPS confirmation of updating of the password of the custom local admin account.
I accessed the password from Entra Admin center which prompted with the MFA challenge through the CA policy requiring MFA for admin roles.
I tested the auto managed password.
Event id 10041 - LAPS detected a successful authentication for the currently managed account and scheduled rotation of the password at the expiry of the grace period.
The Local admin password will rotate automatically after the grace period has expired.
One can also rotate the LAPS password from device actions in Intune.
To view audit events, you can browse to Entra Admin Center > Devices > Audit logs, then use the Activity filter and search for Update device local administrator password or Recover device local administrator password to view the audit events.
Conclusion
Windows LAPS inherits many design concepts from legacy Microsoft LAPS. A key difference is that Windows LAPS is an entirely separate implementation which is native to Windows. One can use Windows LAPS to back up passwords to Azure Active Directory, encrypt passwords in Windows Server Active Directory, and store the password history. Windows LAPS is now built-in into Windows with Windows 10 20H2 and later, Windows 11 21H2 and later, and Windows Server 2019 and later using the most recent security update (released on April 11, 2023).
A couple of things to note here are that when a device is deleted in Azure AD, the LAPS credential that was tied to that device is lost and the password that is stored in Azure AD is also lost. Also, because Windows LAPS can only manage one local admin account on a device at a time, the original account is no longer managed by LAPS policy. In such a situation the new account is backed up and details about the previous account are no longer available from within the Intune admin center or from the Directory that is specified to store the account information.

























Great content & thanks for sharing
ReplyDeleteBest Mulesoft Online Training
Mulesoft Training
ReplyDeleteImpressive Article. Thanks for sharing.
Azure DevOps Training Online
Azure DevOps Online Training
Azure DevOps Online Training in Hyderabad
Azure DevOps Course Online
Microsoft Azure DevOps Online Training
Azure DevOps Training in Hyderabad
Azure DevOps Training
Azure DevOps Training in Ameerpet
ReplyDeleteSuch an informative post Thanks for sharing. We are providing the best services. Click on the links below to visit our website.
Kubernetes Multi-Cloud Training
Kubernetes Multi-Cloud Online Training
Master Multi-Cloud Kubernetes Training
Docker & Kubernetes Multi-Cloud Training
Master Docker & Kubernetes Training
Kubernetes Multi-Cloud Training Hyderabad
Multi-Cloud Online Training Course
Kubernetes Multi-Cloud Training Ameerpet
Docker & Kubernetes Training Institutes
Multi-Cloud Training