Setting up Dynamic groups & Conditional Access policy to enforce MFA as part of Windows 365 Cloud PC configuration in MEM
Windows 365 Cloud PC is the next generation of cloud computing which takes virtualization of the PC to a whole new level. PC-as-a-service or SaaS as Microsoft puts it, is a highly available, optimized, and scalable virtual machine providing end users with a rich Windows desktop experience. It is hosted in the Windows 365 service and is accessible from anywhere, on any device.
Windows 365 service uses the following:
1. Microsoft Endpoint Manager to manage the Cloud PCs.
2. Azure Active Directory (Azure AD) for identity and access control. (HAADJ is also supported)
3. Azure Virtual Desktop for remote connectivity.
4. [Optional] Create Azure network connections, which are links between the Cloud PCs and an on-premises resources.
In this blog we will cover details around creating AAD dynamic groups, AAD conditional access policy to enforce MFA and provisioning of a Windows 365 Cloud PC with AAD identity using Intune.
Configuring Windows 365 Cloud PC in Intune
Cloud PCs are created and assigned to users based on provisioning policies. After provisioning policies are created and assigned to the Azure AD user security groups, the Windows 365 service checks for appropriate licensing for each user before provisioning can commence. This is particularly important because if a license is missing, then the provisioning will fail.
1. Sign in to the Microsoft Endpoint Manager admin center.
2. Navigate to Devices > Windows 365 > Provisioning policies > Create policy.
3. Provide a name and description.
4. Select a join type, followed by the appropriate network.
Note: If you select the combination of Azure AD Join and Microsoft Hosted Network, you must select a region for Microsoft to host your Cloud PC.
5. Select the image from the gallery or if you have a custom image then you can select that.
6. Choose the relevant language & regional setting.
7. Assign to the group of users assigned with the Windows 365 license.
Once you save the profile, provisioning will start.
It can take up to a 45-60 minutes before the provisioning finishes. Once complete, the status will change to Provisioned.
We will now create the AAD groups for assignment of the MEM policies.
Azure AD Dynamic Groups
Normally I would recommend using filters in Intune, but not all workloads support filters at this point.
There are three different categories of groups you can create for Cloud PCs:
1. All Cloud PCs: This type of group is useful for applying policies and configurations to all Cloud PCs in your organization.
2. All Cloud PCs from a specific provisioning policy: This type of group is useful for applying policies and configurations to Cloud PCs based on the same image and location.
3. All Cloud PCs with a specific configuration: This type of group is useful for applying policies and configurations to Cloud PCs based on computing power or internal storage.
For all intent and purposes, I will be covering the process of creating the groups for first 2. Let's see how it is done.
All Cloud PCs:
1. Sign in to the Microsoft Endpoint Manager admin center.
2. Navigate to Groups > New Group.
3. Select the New Group, choose Security for Group type.
4. Give a name & description.
5. Select Membership type as Dynamic Device.
6. Use the following query.
Property = "deviceModel"
Operator = "Contains"
Value = "Cloud PC"
Do validate to check if right devices are populating or not.
All Cloud PCs from a specific provisioning policy:
1. Sign in to the Microsoft Endpoint Manager admin center.
2. Navigate to Groups > New Group.
3. Select the New Group, choose Security for Group type.
4. Give a name & description.
5. Select Membership type as Dynamic Device.
6. Use the following query.
Property = "enrollmentProfileName"
Operator = "Equals"
Value = "<name of the profile>". In my case it is 'MDM LAB Windows 11 Cloud PC'
Just like before, do validate to check if right devices are populating or not.
At this stage, one can start assigning different MDM policies. It is important to note that some policies may not be supported like the use of MDM security baseline. Instead use the Windows 365 security baseline. As of writing this blog, it is still in preview.
Azure AD Conditional Access Policy for enforcing MFA
Since the whole point of Windows 365 Cloud PC is to be accessible from anywhere, it makes sense to enforce MFA against login sessions while accessing Cloud PC through both the Windows 365 Portal and Microsoft Remote Desktop client.
Follow the steps to create the policy:
1. Sign in to the Microsoft Endpoint Manager admin center.
2. Select Endpoint Security > Conditional Access > New Policy.
3. Provide a Name.
4. Under Users and groups, choose Specific users included and select the users or groups that you want to target.
5. Under Cloud apps select the following apps:
Note: By choosing both Windows 365 and Azure Virtual Desktop apps, you make sure that the policy applies to the Cloud PC End-user portal and the connection to the Cloud PC using Remote Desktop client.
6. Under Grant, choose the option to Require multi-factor authentication.
7. Select Create to finish creating the policy. Note: It is recommended to test the policy in Report-only mode first before enabling it.
End user experience & reporting
Intended users can access the Windows 365 Cloud PC assigned to them using Windows365 portal or Microsoft Remote Desktop client. When authenticating to both, they will be challenged with MFA based on the CA settings covered above in this blog. Once the authentication is complete, they will be able to access their Cloud PCs.
Windows 365 Portal on a Windows Device
Remote Desktop client on an Android Device
Remote Desktop client on an Android Device
In order to setup the workspace on Remote Desktop client on Windows, Android, iOS and MacOS devices, use the Get subscription URL details from the Remote Desktop Clients section on Windows365 portal. Once added, user will be asked to authenticate using their corporate UPN and will be challenged with MFA due to CA policy in place.
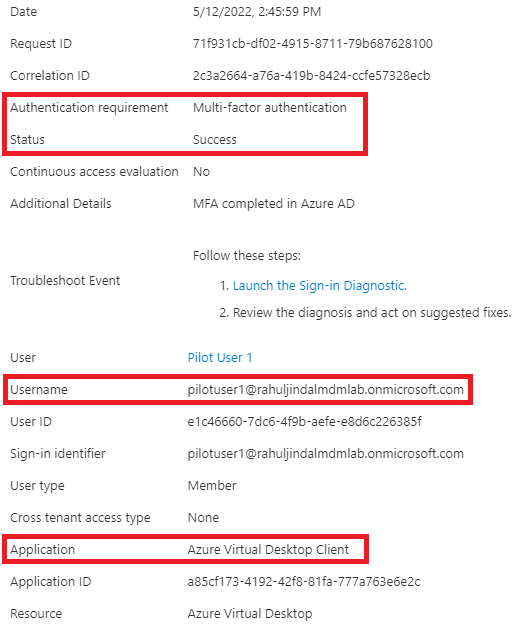
You can verify in the Azure sign-in logs whether CA policy for enforcing MFA against Windows 365 Cloud PC sessions is being logged or not.
Windows 365 Portal on a Windows Device
Remote Desktop client on an Android Device
Conclusion
Windows 365 is fully integrated into the Microsoft Endpoint Manager admin center. Regardless of the join type, Cloud PCs are seamlessly managed in Microsoft Endpoint Manager like any other supported device, including configuration, apps, and updates. Each Cloud PC is assigned to an individual user and is their dedicated Windows device. Provisioning is dependent on license so it does need to be assigned to a user before hand.






















Thank You for this wonderful and much required information Web Application Development Company in USA
ReplyDeleteGood post and very helpful
ReplyDeletekeep writing
If you are faceing account management problem
Contact outbooks teams Outbooks is the perfect solution for businesses who need to keep track of their finances. We provide easy-to-use management accounts software that makes it simple to stay on top of your money. Visit our website today to learn more!
management accounts
Nice article. Please check office workstations for best deal.
ReplyDelete