Why you should enable Tamper Protection in Defender Antivirus?
Probably I am a little late in blogging on this topic, but implementation of Defender policies is incomplete without addressing the requirement of Tamper protection and I wanted to make sure that I covered this.
So what is Tamper Protection and why it should be enabled?
There are a lot of security components within Defender AV which can be configured independantly while some being dependent on other settings. End users can knowingly or unknowingly disable the components or bad actors can disable security controls within Defender AV in an attempt to install malware and steal your data. This is why it is strongly recommended to enable Tamper protection. There are some ways to enable tamper protection, so let's look at each of these methods individually.
Microsoft Defender 365 Portal
You can enable Tamper protection across all your onboarded devices directly from the Defender Portal. However, there are some pre-requisites involved -
- Devices must be onboarded to Microsoft Defender for Endpoint.
- Your devices must be using anti-malware platform version 4.18.2010.7 (or above) and anti-malware engine version 1.1.17600.5 (or above).
- Cloud-delivered protection must be turned on.
Once you have the pre-requisites are in place, follow the steps below to enable Tamper Protection.
1. Sign in on Microsoft 365 Defender portal.
2. Choose Settings > Endpoints.
3. Go to General > Advanced features, and then turn tamper protection on.
Microsoft Intune
If you are managing Windows devices running Windows 11 or Windows 10 OS 1709, 1803, 1809 or later and licensed for Intune, then you can use Intune policies to configure Tamper Protection. It is recommended to use Endpoint Security device profiles to configure the settings.
1. Sign in on Microsoft Endpoint Manager.
2. Choose Endpoint Security > Antivirus > Create Policy
3. Under Platform select Windows 10 & later.
4. Under Profile select Windows security Experience
5. Provide the settings as shown below. (Note: The main setting is to enable Tamper protection here. Rest of the settings are subject to your organization's requirements.)
Microsoft ConfigMgr + Tenant attach
Starting CB 2006, you can manage tamper protection settings on Windows 10, Windows 11, Windows Server 2012 R2, Windows Server 2016, Windows Server 2019, and Windows Server 2022 by using a method called Tenant attach.
Tenant attach enables you to sync your on-premises-only Configuration Manager devices into the Microsoft Endpoint Manager admin center, and then deliver endpoint security configuration policies to on-premises collections & devices. If you have co-management enabled already, you will use the co-management properties to enable device upload. When co-management isn't already enabled, you can use the Cloud Attach Configuration Wizard to enable device upload instead.
In my case Co-management is already enabled so I am just enabling the device upload to MEM admin portal.
1. In the Configuration Manager admin console, go to Administration > Overview > Cloud Services > Cloud Attach.
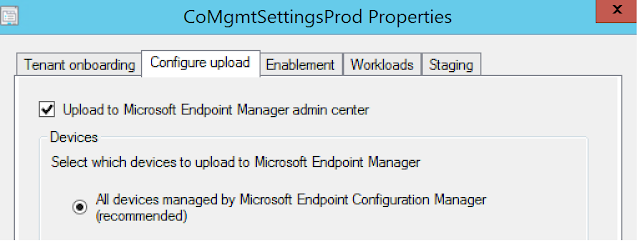
2. In the ribbon, select Properties for your co-management production policy.
3. In the Configure upload tab, select Upload to Microsoft Endpoint Manager admin center. Select Apply.
1. Sign in on Microsoft Endpoint Manager.
2. Choose Endpoint Security > Antivirus > Create Policy
3. Under Platform select Windows 10 and Windows Server (ConfigMgr).
4. Under Profile select Windows Security Experience (preview)
5. Provide the settings as shown below. (Note: The main setting is to enable Tamper protection here. Rest of the settings are subject to your organization's requirements.)
From a security standpoint, it is absolutely imperative that Tamper protection is enabled, even when you have Defender AV running in passive mode or have devices offboarded from Defender altogether. The beauty of this configuration is that even local admins cannot bypass it in an enterprise setting when the policy is being centrally managed. You just need to ensure that you are licensed for Defender for Endpoint. Until next time..




You there, this is really good post here. Thanks for taking the time to post such valuable information. Quality content is what always gets the visitors coming. device security
ReplyDelete