Challenges with enabling ASR rule - 'Block process creations originating from PSExec and WMI commands' on ConfigMgr clients
Last year I had posted a blog on enabling Attack Surface Reduction rules within Microsoft Defender for Endpoint using Intune. This time I will be covering a particular use case that involves one of the ASR rules 'Block process creations originating from PSExec and WMI commands' and challenges around enabling it on devices running ConfigMgr agent.
If you are managing ASR rules using Intune or another MDM provider, then there is little to no problem in enabling ASR rules. However, if you are managing the ASR rules using ConfigMgr or if your devices are running ConfigMgr client, then some of the ASR rules are not supported.
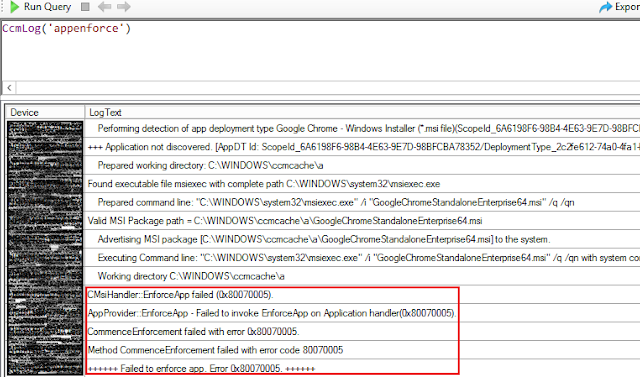
I am currently working on an implementation project of Defender for Endpoint where devices are in Co-managed state and the ASR rules are being deployed using Intune. As part of testing, I enabled all the ASR rules and all of a sudden started to see application installations to fail. My first clue was seeing 'Access denied' errors in Appenforce.log.
I checked in Microsoft Defender 365 Portal and noticed detections under Reports->Attack surface reduction rules being reported.
Unfortunately, the detection didn't give me any relevant details so I switched to good old Advanced Hunting to pull ASR device events.
The action type corresponds to the ASR rule 'Block process creations originating from PSExec and WMI commands'. On further investigation I stumbled upon Microsoft's official documentation & warning on this.
As I see it, there are 3 ways to address this.
1. Disable the ASR rule altogether.
2. Run the ASR rule in Audit mode and monitor the events for analysis.
3. Based on the analysis of the ASR rule, add the necessary exclusions.
I decided to go with the 3rd option and add Msiexec, WMI processes to the existing exclusions I had put in place earlier. Now some may argue that it is not advisable to add these two in exclusions (to which I agree to some extent), but at the end it all boils down to your setup and business requirements. With having control over application installations through ConfigMgr and all Defender policies turned on the devices that are being used by users with Standard permissions, this seemed like a safe bet.
Once, I added the exclusions, there were no more ASR events generated for 'Block process creations originating from PSExec and WMI commands' rule in relation to Msiexec, WMI and application installations from ConfigMgr went through normally.
If you want to know the compatibility matrix for all the ASR rules then here is information provided by Microsoft.
Conclusion
Attack surface reduction rules that target executable files and scripts attempting to download\run files, can sometimes affect legitimate applications as well. I really hope that all ASR rules can become compatible across all deployment methods, especially ConfigMgr, but until this happens, it is important to run these rules in Audit mode first to access the impact of these rules and then add necessary exclusions to suit your business needs.













Comments
Post a Comment