How to Block Windows Hello for Business using Account Protection policy in Intune
In one of my
earlier blogs,
I had covered how to setup Windows Hello for Business (WHfB). In this blog I want
to cover how you can block it completely using Intune.
Recently, I
had a requirement where the customer wasn’t ready to enable WHfB in their
organization. While the feature can be disabled tenant wide, it only applies
during the Out of Box Experience or OOBE at the time of device enrollment. Also, the tenant wide setting will not
apply if a device is already enrolled. One obviously needs to meet the pre-requisites
to be able to use the feature and you can refer to the Microsoft's official link.
Now if you
want to perform an Autopilot reset to re-provision a device, then WHfB
will get enabled by default. This
is because according to Microsoft,
“When Windows 10 was released to general availability, Microsoft changed the
behavior of the Office 365 Azure AD stack. When a user selects the option to
join a work or school network, the device is automatically joined to the Office
365 tenant’s directory partition, a certificate is issued for the device, and
it becomes eligible for Office 365 MDM if the tenant has subscribed to that
feature.” This results in Hello for Business being enabled by default.
When you perform an Autopilot reset, it doesn’t do a factory reset, thus not taking the process all the way back to OOBE, and instead only wipes the user data, files and settings. It retains the connection to Azure AD and Intune which allows re-provisioning by applying device and user apps and configuration policies. A healthy tip from the field is to use an Enrollment Status Page (ESP) to block the use of the machine to ensure everything applies before desktop session loads.
Microsoft introduced
Endpoint security node in Intune to configure device security and
to manage security tasks for devices when those devices are at risk. One of the
security type is Account Protection which helps you protect the identity and
accounts of your users. The account protection policy is focused on settings
for Windows Hello and Credential Guard, which is part of Windows identity and
access management. Please note that at the time of writing this blog, this
policy type was still in Preview.
How to
create Account Protection Policy?
2. Browse to Endpoint Security – Account Protection – Create a Policy
3. Select Platform as Windows 10 and later.
4. Select Account Protection (Preview) as Profile Type and then hit Create.
5. File the relevant fields like Name, Description and click Next.
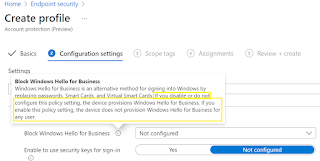
6. Under Configuration Settings->Account Protection-> Block Windows Hello for Business, select Enabled. Make a note of the information message below.
7. Add the necessary Scope tags (if any) and then assign to a device based group.
It should then look something like this.
Conclusion
You have
the option of using Identity Protection policy or a PassportForWork
CSP to do the same thing, however, in my experience, blocking WHfB using Account
Protection policy has given consistent results.
References




Nice post! I wonder if such Enterprise mobile application development and management protocols can be applied to Android and iOS smartphones.
ReplyDelete