Passkeys for macOS and addressing the phishing resistant authentication registration loop
For the last couple of days, I have been working on securing my own tenant and as a result of this, I wanted to enable passkeys for all my test accounts. Passkeys (FIDO2) not only improves productivity and provide better security, but also make the authentication process seamless by eliminating the need for entering a username or password. This can be achieved through both FIDO2 security key and Microsoft Authenticator. Due to this fact, Microsoft and its partners are investing in both synced and device bound passkeys for work accounts. However, and during my own testing, enabling passkey on the user's side can go into a loop when trying to add a passkey in Microsoft Authenticator application. This may not be a case for every tenant, but if you have conditional access policies created that specifically leverage phishing-resistant authentication strength, then you will most likely run into this issue. Luckily there are some work arounds available and require further actions.
In this blog post, I explore the configuration of enabling passkey for authenticating against cloud resources on macOS and addressing the registration loop.
Let's start by enabling passkeys in the Microsoft Authenticator in the tenant
Since passkeys can be added in the Microsoft Authenticator app and the fact most organizations enforce MFA for their users through this app, the application naturally becomes the method of choice for enabling passkeys for the end users. This is how you can enable it -
1. Sign in to the Microsoft Entra admin center.
2. Navigate to Protection > Authentication methods > Policies.
3. Under the method Passkey (FIDO2), select All users or Add groups to select specific groups.
4. Next on the Configure tab, set the values as shown below -
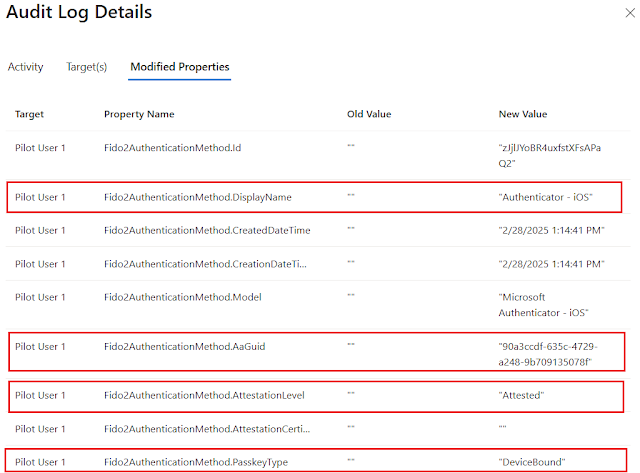
Note: When the user is registering a passkey in the Authenticator, attestation verifies that a legitimate Authenticator app has created the passkey by using Apple and Google services. By selecting Microsoft Authenticator under Restrict specific keys (when configured to 'Allow'), AAGUID for the Microsoft Authenticator apps for both Android and iOS will get added automatically.
5. Hit 'Save' and you are done with enabling passkeys in the tenant.
Next up is to enforce sign-in with passkeys in Authenticator using built-in phishing-resistant authentication strength policy.
1. Sign in to the Microsoft Entra admin center.
2. Navigate to Protection > Authentication methods > Authentication strengths.
3. Select New authentication strength.
4. Provide a name.
5. Select Passkeys (FIDO2), and then select Advanced options.
6. Select Microsoft Authenticator (In preview as of writing this blog). You can also add AAGUIDs manually if needed.
7. Review and save the policy.
Now that the authentication strength is created for Passkeys (Microsoft Authenticator), it is time to create relevant conditional access policies. There are actually 2 policies and both are recommended to ensure that users don't hit a registration loop for configuring passkeys.
Conditional Access Policies
Phishing resistant Authenticator to access a desktop OS
1. Sign in to the Microsoft Entra admin center.
2. Select Protection > Conditional Access.
3. Select Policies > New policy to create a new policy.
4. Create a new policy and specify the intended targeted users\groups\roles.
5. Under Target resources, select All resources.
6. Under Network, you can configure locations as needed.
7. Under Conditions > Device Platforms, include Windows, macOS, and exclude Android and iOS.
8. Under Grant controls, select the Passkeys (FIDO2) authentication strength created for Microsoft Authenticator.
9. Enable it and save the policy. Note: It is always a good idea to test in report-only mode in production environments.
Phishing resistant Authenticator to access for Mobiles
1. Sign in to the Microsoft Entra admin center.
2. Select Protection > Conditional Access.
3. Select Policies > New policy to create a new policy.
4. Create a new policy and specify the intended targeted users\groups\roles.
5. Under Target resources, select All resources.
6. Under Network, you can configure locations as needed.
7. Under Conditions > Device Platforms, include Android, iOS and exclude Windows, macOS.
9. Enable it and save the policy. Note: It is always a good idea to test in report-only mode in production environments.
Configuration in action..
When a user tries to access cloud apps like Teams, Outlook on a macOS or a Windows devices, after providing the credentials, they are immediately asked to register for passkeys.
At this stage, the user needs to follow the steps on the mobile phone to create a passkey.
The user needs to click on sign in and allow Authenticator to autofill password and passkeys in the settings in case of iOS.
That's it. You are done creating the passkey on the mobile.
Now come back to the app on the macOS and you should be able to finish the configuration and use the passkey to authenticate. Note: Unrestricted Bluetooth access is required for authentication through passkeys to work.
The registration and authentication can be verified in Entra ID.
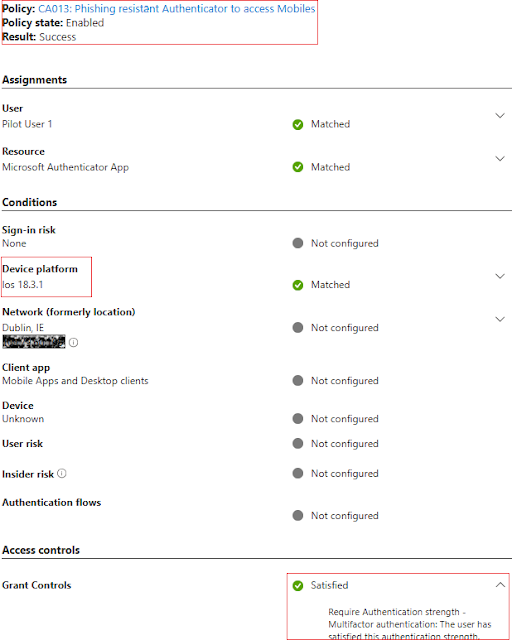
You can also verify whether CA policies are enforcing correctly or not.
Final thoughts..
Passkeys is a great addition to the password-less authentication methods, but it may be a good idea to get a jump start and prepare the end users for the change to come. Normally, the best way is to run internal campaigns to help users adopt passkeys and then control the rollout by targeting specific apps instead of all in one go. Another thing to note is that in case of new users, who are registering sign-in info for the first time, can be assigned Temporary Access Pass (TAP) that can help them finish up setting passkeys. However, with the current set of conditional access policies (as covered in this blog), users will only be allowed to use TAP on mobile platforms. Lastly, you can use the Authenticator camera to register and authenticate with passkeys. This option is useful if your organization doesn't push the system camera app to Android Work Profile.
Until next time..
















.jfif)
.jfif)
.jfif)
.jfif)
.jfif)
.jfif)
.jfif)










Comments
Post a Comment