The fine balance between Device Control Policy & removable storage

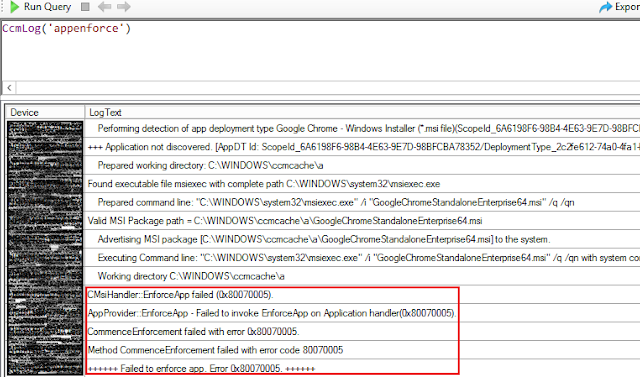
Microsoft Defender for Endpoint Device Control protects against data loss by monitoring and controlling media use of removable storage devices and USB drives. It is part of the Attack Surface Reduction profiles which enables auditing, read, write or execute access to removable storage. Once you enable Device Control policy, you can find the device control report in the Microsoft 365 security center . However, please note that the device control report can have a 12-hour delay from the time a media connection occurs to the time the event is reflected in the card or in the domain list. I recently came across a situation where there was a requirement for allowing the use of USB screen sharing solutions like Barco Clickshare . They are normally used in VC Meeting rooms and the process for activation requires plugging them into a laptop and running the application executable. To ensure the use of such devices, you either disable the Device Control policy or simply create a whitelist. C...