Intune - Microsoft Edge browser settings & extensions
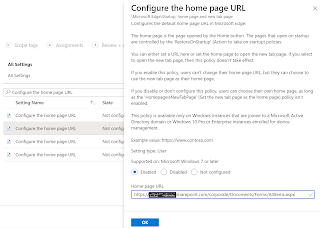
In this blog I will cover some of the settings of Microsoft Edge browser configured using built in administrative templates in Intune. Using Intune to manage and enforce policies is equivalent to using Active Directory Group Policy or configuring local Group Policy Object (GPO) settings on user devices. For a complete list of Microsoft edge policies, you can check the link here . Let’s begin 1. Sign-in to the https://endpoint.microsoft.com 2. Browse to Devices – Windows – Configuration profiles 3. Click Create Profile 4. Choose Windows 10 and later as Platform 5. Choose Administrative Templates as Profile type 6. Click Create 7. Give a name 8. Use the search field ("Search to filter items ...") to find a spec...


